Kimsuky Arsenal Exposure: Multi-format Trojan Analysis
Latest Research|November 20, 2024
Overview
Recently, SecAI has detected a series of targeted attacks launched by Kimsuky since 2024, showing high activity levels. This includes samples related to security to the South Korean Embassy in China in April, invoice-related samples to a construction company in June, and lecture-related samples to a well-known South Korean university in July. Through long-term tracking and analysis, this group has been stealing information and conducting remote control activities by setting up a large number of phishing websites and sending phishing emails with samples that induce clicks with names of interest to the victims. After collecting various attack samples from Kimsuky, it has been found that the group has the following characteristics:
- Using phishing websites to deceive victims into revealing account passwords, involving popular websites in South Korea, the United States, and Japan, as well as email and tax insurance-related Korean websites.
- Using phishing emails to deliver various types of samples involving Windows, Linux, and Android systems, with the highest proportion being Windows. The samples use multiple scripts for multi-stage downloading, decrypting, or loading and executing. The samples also disguise themselves with names that interest the victims to induce clicks and execution.
- Using a large number of compromised sites, public file hosting services, and mimicking legitimate websites to store and download encrypted payloads, then using various scripts for downloading and decrypting to ultimately obtain information and remote control.
- SecAI, through the analysis of related samples, IPs, and domain names, has extracted multiple relevant IOCs for threat intelligence detection. SecAI's Network Detection and Response (SecAI NDR), Threat Intelligence Cloud API, support detection of this attack event.
Attack Group Analysis
1. Profile of the Attack Group
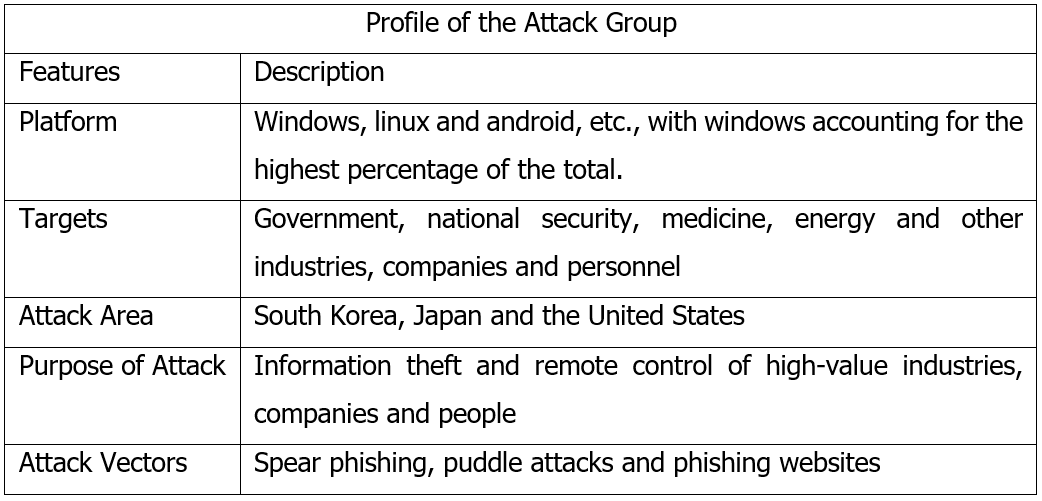
Kimsuky, also known as APT43, APT-Q-2, Velvet Chollima, Black Banshee, Thallium, Sparkling Pisces, etc., has been operating since 2012 and is supported by the North Korean government. It mainly targets South Korea and its allies such as Japan and the United States, using spear-phishing, watering hole attacks, and phishing websites for intrusion. The main goal is to steal high-value information for intelligence gathering, with interests in industries including South Korean government, national security, pharmaceuticals, energy, and education.
2. Technical Features
Kimsuky organization generally adopts the method of first establishing phishing websites to obtain account passwords, and then sending phishing emails to induce the execution of malicious samples. That is, first establish phishing websites to induce victims to enter email account passwords, and then use the obtained email account passwords to send phishing emails to high-value users. The phishing emails embed malicious samples initiated by different types of file formats, such as lnk, xls, doc, or iso files, etc., which run hidden by a series of scripts and ultimately execute C&C commands.

2.1 Account and Password Theft
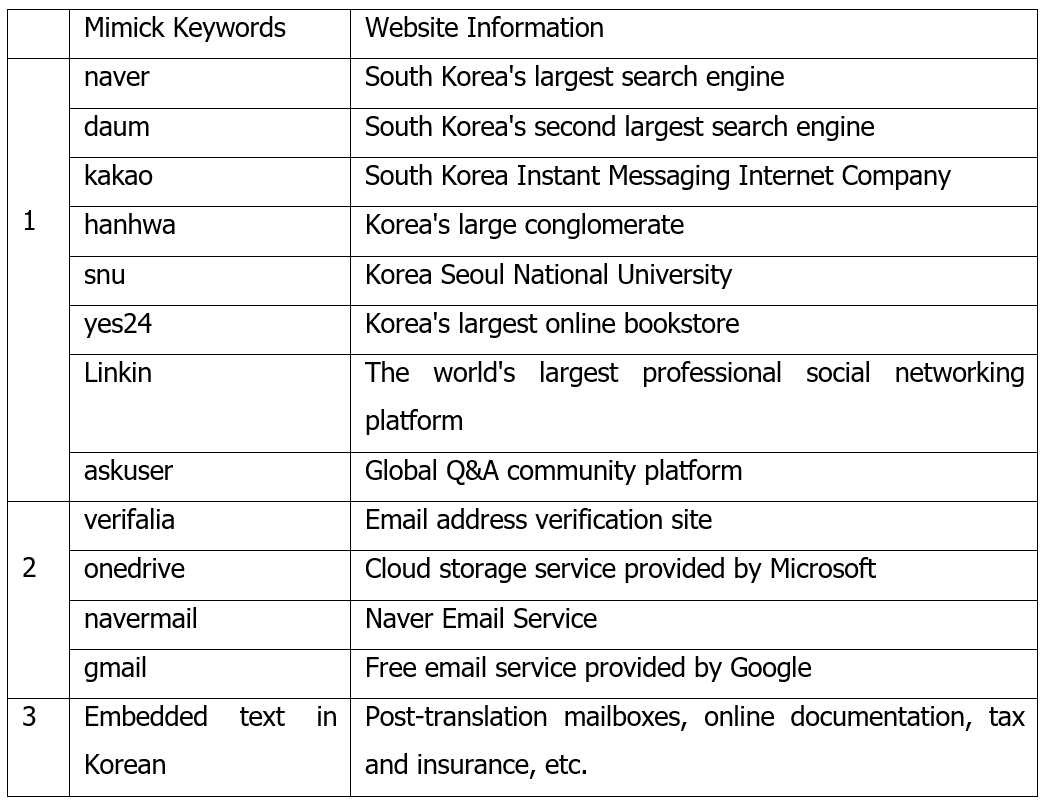
The Kimsuky organization initially employs phishing websites to conduct large-scale cyber phishing, acquiring victims' email account passwords to prepare for the subsequent email delivery. The mimicked phishing websites are broadly categorized into three types: 1. Imitating well-known websites in South Korea, the United States, and Japan; 2. Imitating well-known email websites; 3. Phishing links containing Korean text. The characteristics of the mimicked keywords are shown in the table below:
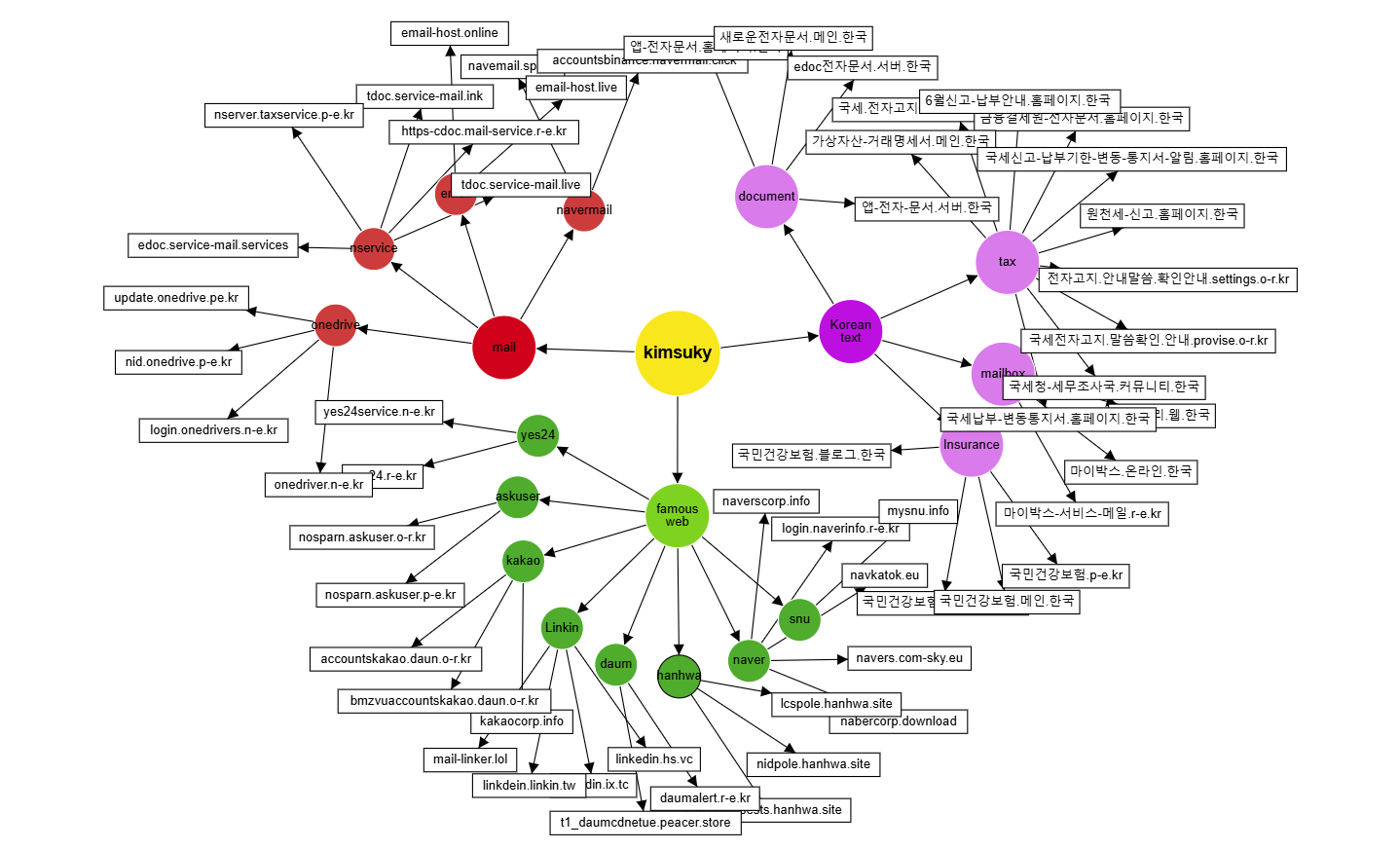
Based on the characteristics of the phishing websites, the assets collected by this organization are categorized as shown in the figure below:
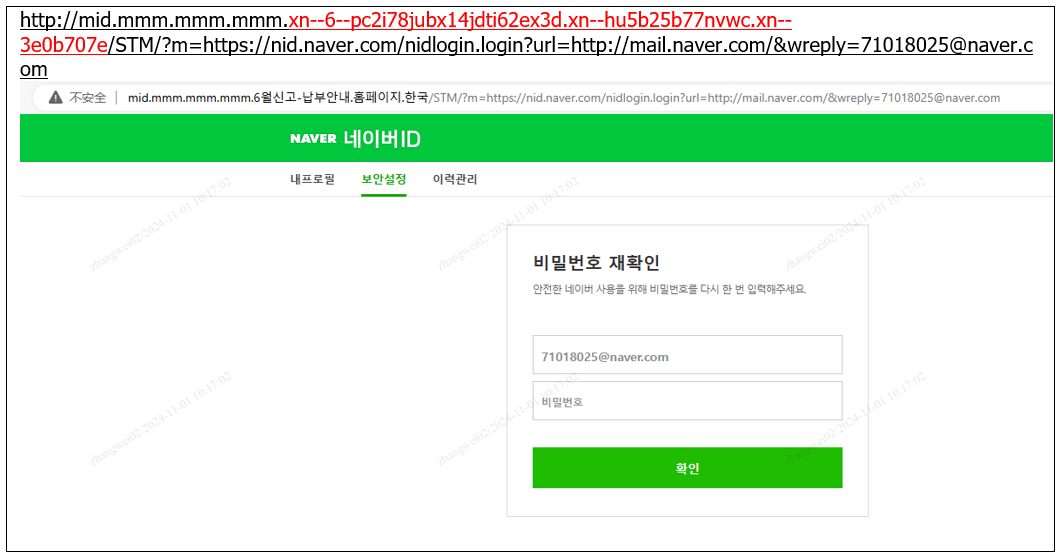
Recently, the phishing interface set up by Kimsuky is shown below. By forging the login for Naver email, it includes Korean text ("June Declaration - Payment Guide. Home. South Korea"), inducing victims to enter their account passwords.
2.2 Email Delivery
After successfully stealing account passwords through a large number of phishing web pages, the organization filters out high-credibility email accounts from the collected accounts. They use these email account passwords to send forged phishing emails to high-value account emails, with the aim of bypassing email gateway interception, thereby ensuring the high disguise and click-through rate of the emails. Moreover, before sending emails containing actual payloads, they also send some normal emails to lower the victim's guard, and finally send emails with attached malicious samples to induce clicks, as shown in the figure below:
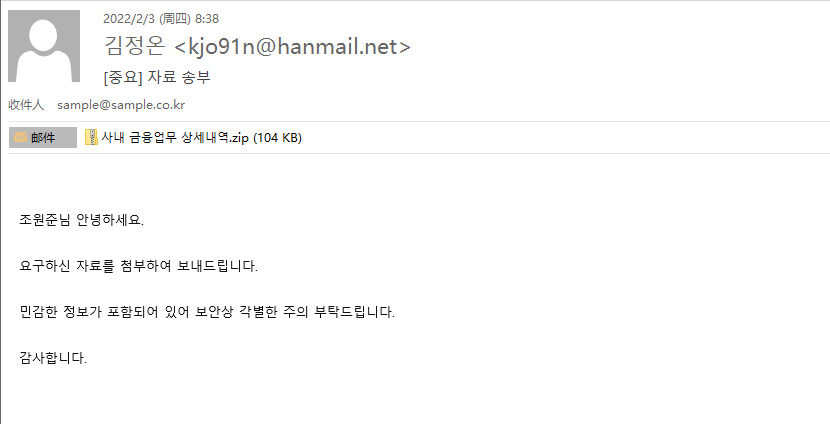
The attached files in the phishing emails are often compressed packages. After decompression, the file types include a variety of formats, such as lnk files, iso files, xls files, doc files, chm files, msc files, and js files on the Windows system, among others. These files typically embed scripts like cmd, bat, vbs, js, and PowerShell, which call each other to execute actions such as downloading, decrypting, or running, ultimately to carry out the core payload.

2.3 Sample Construction
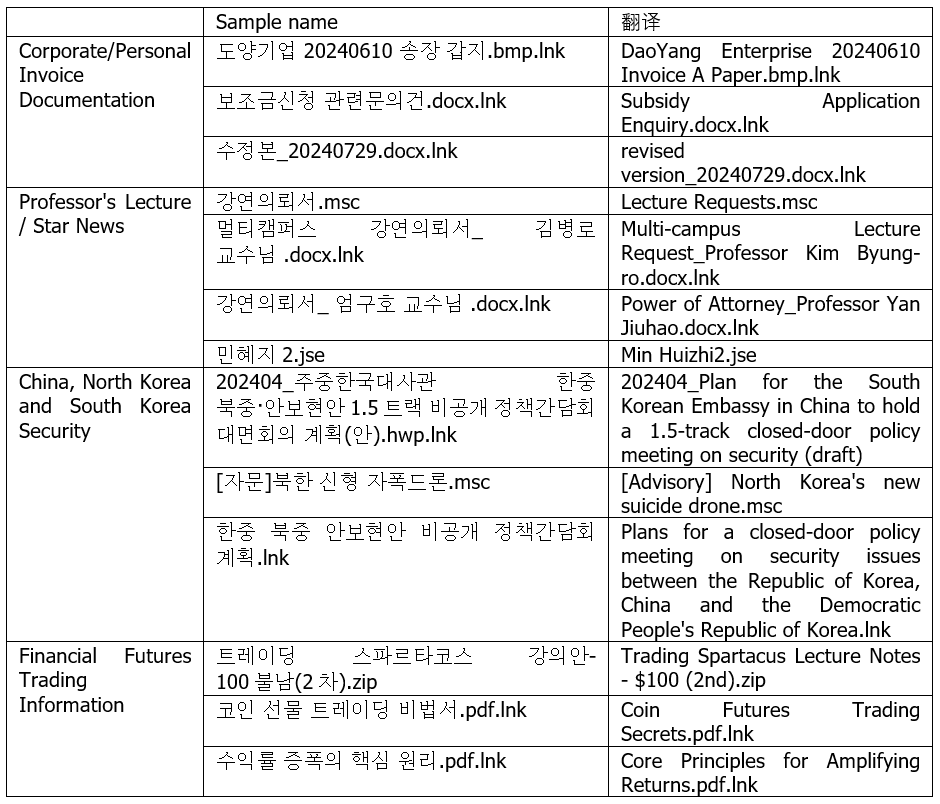
The samples embedded in phishing emails are disguised with names that interest the victims to induce them to click and run. The following are the collected sample names, and the forged titles of the samples are mainly divided into: Corporate/Personal Invoice Documents; Professor Lectures/Celebrity News; China-North Korea-South Korea Security Issues; Financial Futures Trading Information, etc.
3. Asset characteristics
Kimsuky further controls the victim's host by using scripts to release, decrypt, or download malicious files. However, the websites from which files are downloaded generally fall into three categories, as shown in the table below:
- Compromised websites, which are mainly sites with poor security awareness, such as universities and funding organizations;
- Public file storage services, primarily Google, Dropbox, and GitHub file storage services, where files are usually encrypted before being uploaded, and can only be executed normally after being decrypted with a specific algorithm;
- Maliciously constructed websites, which mainly imitate well-known websites and are not easily detected in traffic alongside their samples.

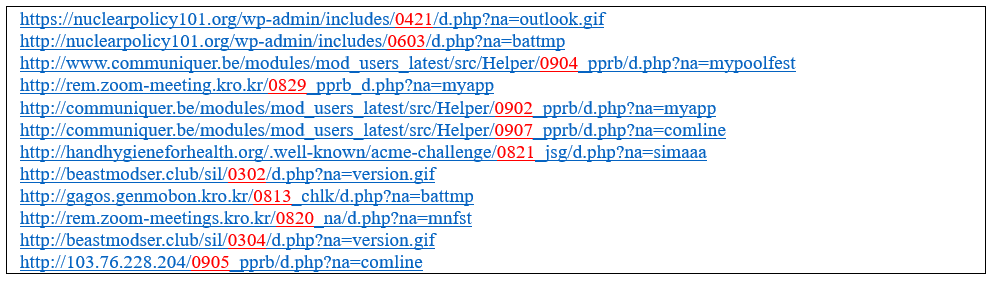
At the same time, Kimsuky has consistently used a certain pattern in URL formats, using PHP endings and meaningful parameter key-value pairs to forge normal URL communications.

In addition to this, since 2024, Kimsuky has been infecting or creating malicious websites using urls in the {mmdd} format, suspected of marking the date of their creation, consisting of directories via separate directories or directories appended with underscores and short strings, as shown in the following table.
C&Cs are mostly based on dynamic domain names, with the main domain name using Korean second-level dynamic domain names such as n-e.kr, p-e.kr, r-e.kr, o-r.kr and kro.kr, which are formed by splicing using well-known words. However, the overall share of C&C in this category has weakened recently, with the share of free domain names such as site, store, online, me and shop gradually increasing.
Reference Links
- https://mp.weixin.qq.com/s/OaECtSaeClPzFHslN_WamA
- https://asec.ahnlab.com/ko/30980/
- https://medium.com/s2wblog/unveil-the-evolution-of-kimsuky-targeting-android-devices-with-newly-discovered-mobile-malware-280dae5a650
- https://www.security.com/threat-intelligence/springtail-kimsuky-backdoor-espionage
Appendix - IOC
Domain
- mid.mmm.mmm.mmm.6월신고-납부안내.홈페이지.한국(phishing)
- evangelia.edu(compromised)
- trusteer.ink(C&C)
- nzzstore.site(C&C)
- mngrdp.site(C&C)
- koreaillmin.atwebpages.com(C&C)
Hash
7d766cbd60b2184b4181eb83562d5a406b848adddfa20842a073c25d3f1fe853 1099a77b2de97f26605b32e25e806b636e36103a3b8d601e1e30b15c922de578 ea332de382c843e4d862323466fee3d94c3722e3e9e61c00bf2bdf379a7087af 8028b918d06cf3635e7e77d29cb0a4622d8cf4ee30881fb297435f7328ff45e4 35ddb63c0729a7e3019c026865ea195607a51943d8867607a26c006f0df6e594 06e2ab3fe5afc927642244644dfddb0f920ff1ab11c5e5631e26dbd62ed6978a 5d25e53b59bd2dcf234c6819f8cd294efe6d943d04625b9d575002362794e74a 6263530f1bde08b13872252fa1e90efc0ac5c8d433db6931316c8eb7322d23c4 30584f13c0a9d0c86562c803de350432d5a0607a06b24481ad4d92cdf7288213
Copyright © SECAI PTE LTDAll rights reaserved.Terms & Conditions.

