Malware Analysis of Kimsuky's Attacks - jse
Latest Research|January 9, 2025

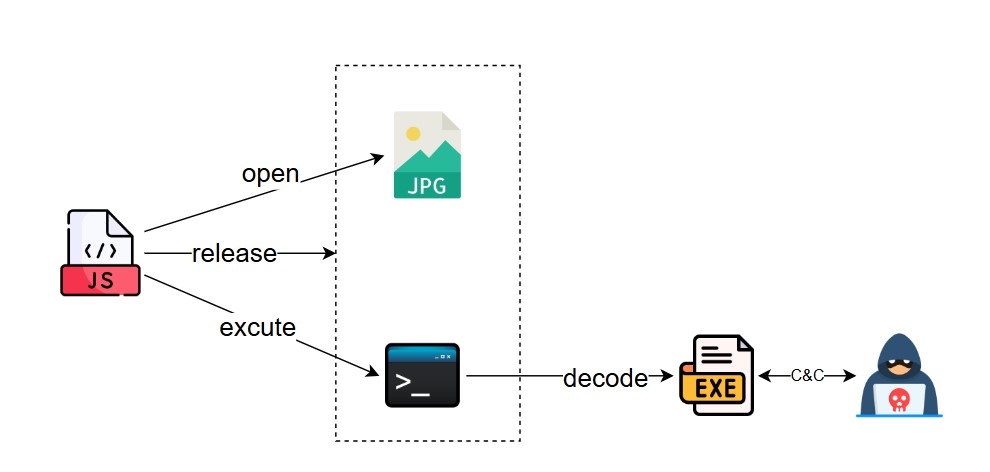
JSE file is a JavaScript Encoded file extension, an encrypted or encoded version of a JS file (JavaScript file) used to protect the source code of a script from unauthorised viewing and modification. The malicious sample releases the jpg file as well as encrypted powershell script through the obfuscated js script, and after executing the powershell script, it will release the VMP-hulled PE file to achieve C&C remote control. The whole flowchart is shown below:
Analysing the jse file revealed a large amount of obfuscated code and encrypted data.

By de-obfuscating and omitting the encrypted data (where the data is too large to avoid interfering with the use of ... is omitted) as shown below:

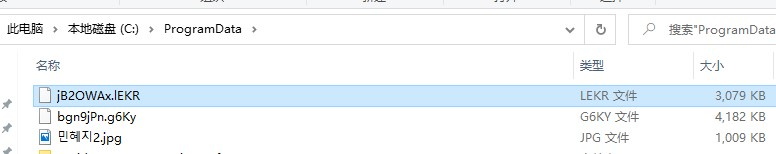
Main function: release open jpg as well as bgn9jPn.g6Ky (base64 encrypted data), then use powershell to decrypt the bgn9jPn.g6Ky data file and save it to jB2OWAx.lEKR (exe type).
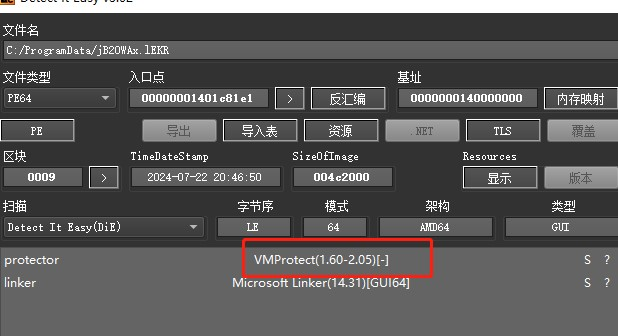
Eventually, jB2OWAx.lEKR is launched using powershell, shelled using VMP, and will be followed by access to C2:pmlroma.kro.kr for back-connection control.
Background of the Research
Recently, SecAI has detected a series of targeted attacks launched by Kimsuky since 2024, showing high activity levels. This includes samples related to security to the South Korean Embassy in China in April, invoice-related samples to a construction company in June, and lecture-related samples to a well-known South Korean university in July. Through long-term tracking and analysis, this group has been stealing information and conducting remote control activities by setting up a large number of phishing websites and sending phishing emails with samples that induce clicks with names of interest to the victims.
Kimsuky, also known as APT43, APT-Q-2, Velvet Chollima, Black Banshee, Thallium, Sparkling Pisces, etc., has been operating since 2012 and is supported by the North Korean government. It mainly targets South Korea and its allies such as Japan and the United States, using spear-phishing, watering hole attacks, and phishing websites for intrusion. The main goal is to steal high-value information for intelligence gathering, with interests in industries including South Korean government, national security, pharmaceuticals, energy, and education.
Learn more about our latest research on Kimsuky: Kimsuky Arsenal Exposure: Multi-format Trojan Analysis
Copyright © SECAI PTE LTDAll rights reaserved.Terms & Conditions.

